Chrome and Firefox are adding some extra protections to their systems to protect users from a nasty phishing trick.
Normally, when you click on a link to a site, you expect to be taken to that particular site. Thanks to a researcher, however, it has been discovered that it's not always the case due to a vulnerability of most browsers in the way they translate special characters.
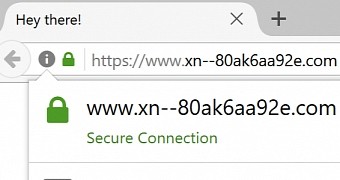
For example, a website address that starts with xn-- tells your browser that the domain name is encoded using Punycode, which allows special characters to be displayed. This ability is quite important because a large part of Internet users don't speak English, or it's not their first language, and their mother tongues include such special characters.
This, however, also lets cybercriminals execute what is called a homograph attack. Basically, it tricks the browser into believing a certain domain that includes special characters is actually a different domain, one that people trust. By spoofing the domain, users will believe they are in the right location.
Chrome and Firefox will display a mess of characters as the right URL. Furthermore, the scammer can even apply for an SSL certificate for the Punycode name and, given what has surfaced in recent scandals, will likely even get it. Then, you'll find yourself on a site you think you know, with a "secure" tag near the address bar, indicating that everything is right in the world. What is the next thing you do? You log in. What is the next thing that happens? The cybercriminals steal your credentials.
Chinese security researcher Xudong Zheng came up with a proper example of this situation with the site epic.com. By using the Punycode trick, the fake site looks legit, complete with the SSL certificate to back it up.
Fixes, coming right up
Homograph attacks have been around for the better part of the decade, and it's proven to be a difficult technique to fight against. Chrome and Firefox, however, may soon get some protection.
Chrome Canary has already been updated with a new feature that protects users from such attacks. Canary, as you may know, is the experimental version of the browser, so it may take a while before the consumer version gets the update. Once they do, however, they will be protected automatically.
Mozilla is also protecting its users. In fact, they can go ahead and do a little tweaking to get the desired effect. You'll just have to type about:config in the address bar, agree to the warning Firefox displays and enter Punycode in the search box that shows up, as well as a line that reads network.IDN_show_punycode. This means that you will start seeing the proper Punycode addresses instead of the encoded versions.
“In this vulnerability an anti-phishing mechanism wasn’t implemented properly in some web browsers, and like in many other cases, improper implementation renders the mechanism ineffective, in this case exposing users to phishing attacks that are hard to identify. In most of the cases these scenarios end with account takeover, where the attacker obtains control of the user’s account," said Itsik Mantin, Director of Security Research at security company Imperva.
"In order to protect website users, forcing them to use strong passwords and to replace them frequently is insufficient, since in this case it would be completely ineffective to prevent the attack. Site administrators should assume that the credentials of some of their users were stolen (which in almost 100% of the cases will be true), and take adequate measures to identify account takeover, like irregular device, irregular geo-location or abnormal activity in the account.”
 14 DAY TRIAL //
14 DAY TRIAL //