Google has released today Chrome 53.0.2785.89, the first stable version of the 53.x branch, which features a slew of features dedicated mainly to web developers.
Chrome 53 is the version in which Google will start blocking blocking Flash tracking for better battery life and performance, and the version which adds the Material Design UI for Chrome on Windows, after the look was introduced for the first time on the Mac version in Chrome 52.
Despite these changes, just in like Chrome 52, in version 53, Google engineers focused on web development standards-related features mostly.
Shadow DOM V1
Considered a major feature added in this release, the Shadow DOM is strictly for developers.
Chrome already features support for Shadow DOM V0, which was a very early version of the standard that browser vendors implemented in different ways. Google says that multiple browser vendors have now agreed on how to handle Shadow DOM, which is the current V1.
Shadow DOM is a W3C-sanctioned standard for embedding components inside web pages without the embedded and the parent code interacting and messing each other up.
Developers working on ten-page sites will probably never need Shadow DOM, but developers working on sites with thousands and millions of pages with tens or hundreds of styles and components will find its modular features very useful.
Google says they'll support Shadow DOM V1 and Shadow DOM V0 at the same time in Chrome until most users have migrated to the newer version.
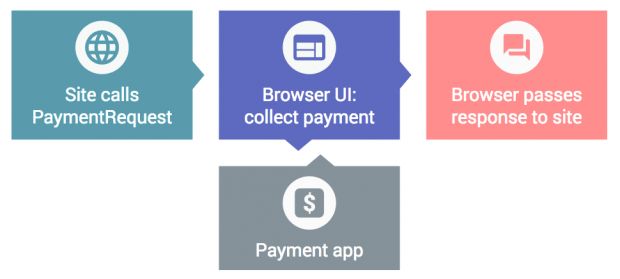
PaymentRequest API
A glorified autofill feature, the new PaymentRequest API implemented in Chrome 53 allows developers to simplify the way in which users fill out payment forms.
The API provides a secure method of saving user details in the browser and then filling them in whenever the user navigates to a checkout page.
The PaymentRequest API works with Chrome and Android apps, and while it looks incredibly useful at first glance, there is also the issue of banking trojans that could scrape this data for valuable content.
Chrome for Android changes
There are two cool features included in the Android version of Chrome. First, developers will be able to change the Chrome icon that appears in the notifications bar when the browser triggers an alert.
Developers can change this to a cat, buffalo, star, or whatever they want, allowing site owners to build more personal experiences for their visitors. This Chrome feature is only supported with Android devices running Android 6.0 (Marshmallow) or later.
Secondly, Chrome for Android now supports an "autoplay" attribute for the HTML5 video tag, but there's a catch.
This attribute works only if the "muted" attribute is used as well. This means that videos will start automatically on Android devices if the developer has muted the movie.
If the sound is turned on by default, the video won't start out of the blue when scrolling down a page, most likely to avoid scaring or annoying a site's visitors.
< source src="video.webm" type="video/webm" / >
< source src="video.mp4" type="video/mp4" / >
< /video >
Security bugs and other smaller updates
As with all Chrome releases for the stable branch, Google's security team contributed bugfixes that addressed a wide range of vulnerabilities and issues.
Based on internal code audits and bugs reported by the infosec community, Google engineers fixed 33 security issues and handed out $56,500 to contributors.
Below is the full list of security bugs, followed by a selection of smaller changes. For the full list of modifications, check out Chrome 53's full changelog.
Users can update Chrome using the built-in update tool, or they can download a fresh copy from Google's site or one of the Softpedia download mirrors for Windows, Mac, and Linux.
[$7500][628942] High CVE-2016-5147: Universal XSS in Blink. Credit to anonymous
[$7500][621362] High CVE-2016-5148: Universal XSS in Blink. Credit to anonymous
[$7500][573131] High CVE-2016-5149: Script injection in extensions. Credit to Max Justicz (http://web.mit.edu/maxj/www/)
[$5000][637963] High CVE-2016-5150: Use after free in Blink. Credit to anonymous
[$5000][634716] High CVE-2016-5151: Use after free in PDFium. Credit to anonymous
[$5000][629919] High CVE-2016-5152: Heap overflow in PDFium. Credit to GiWan Go of Stealien
[$3500][631052] High CVE-2016-5153: Use after destruction in Blink. Credit to Atte Kettunen of OUSPG
[$3000][633002] High CVE-2016-5154: Heap overflow in PDFium. Credit to anonymous
[$3000][630662] High CVE-2016-5155: Address bar spoofing. Credit to anonymous
[$3000][625404] High CVE-2016-5156: Use after free in event bindings. Credit to jinmo123
[$TBD][632622] High CVE-2016-5157: Heap overflow in PDFium. Credit to anonymous
[$TBD][628890] High CVE-2016-5158: Heap overflow in PDFium. Credit to GiWan Go of Stealien
[$TBD][628304] High CVE-2016-5159: Heap overflow in PDFium. Credit to GiWan Go of Stealien
[$n/a][622420] Medium CVE-2016-5161: Type confusion in Blink. Credit to 62600BCA031B9EB5CB4A74ADDDD6771E working with Trend Micro's Zero Day Initiative
[$n/a][589237] Medium CVE-2016-5162: Extensions web accessible resources bypass. Credit to Nicolas Golubovic
[$3000][609680] Medium CVE-2016-5163: Address bar spoofing. Credit to Rafay Baloch PTCL Etisalat (http://rafayhackingarticles.net)
[$2000][637594] Medium CVE-2016-5164: Universal XSS using DevTools. Credit to anonymous
[$1000][618037] Medium CVE-2016-5165: Script injection in DevTools. Credit to Gregory Panakkal
[$TBD][616429] Medium CVE-2016-5166: SMB Relay Attack via Save Page As. Credit to Gregory Panakkal
[$500][576867] Low CVE-2016-5160: Extensions web accessible resources bypass. Credit to @l33terally, FogMarks.com (@FogMarks)
[642598] CVE-2016-5167: Various fixes from internal audits, fuzzing and other initiatives.

 14 DAY TRIAL //
14 DAY TRIAL //