A Chinese company that markets itself as a mobile app promoter has been cheating its clients by deploying adware to install their apps on unsuspecting victims.
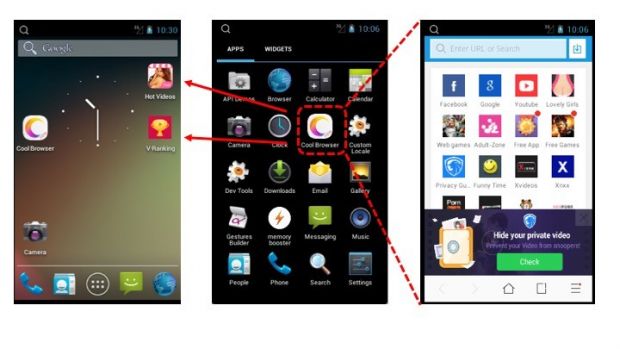
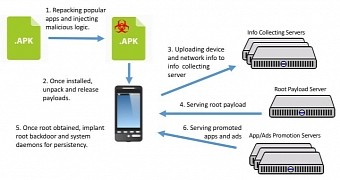
The company, named NGE Mobi/Xinyinhe, activating in China and Singapore, has been using popular apps, repackaged with the malicious adware code, which it distributes through unofficial Android app stores.
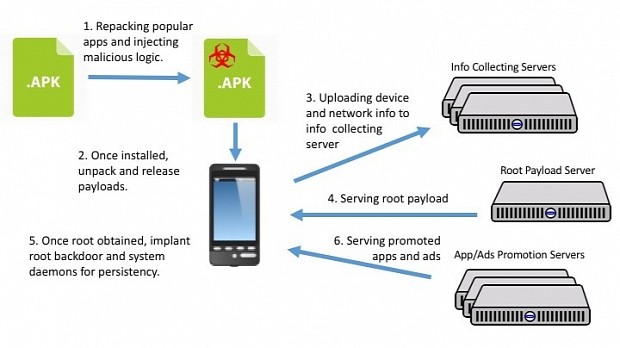
When users install these apps on their smartphones, the adware comes to life, collects information about the device, sends it to a C&C server, and then waits for new commands.
The adware can gain root access and boot persistence
When the server answers, the app moves to install a root backdoor and a series of system daemons that allow it to survive system reboots.
Here is where the fun begins, because once the adware is firmly implanted on the victim's phone, it starts serving apps and ads, all from NGE Mobi/Xinyinhe's portfolio.
As FireEye found out in their research, most of the times pornographic apps and ad interstitials are displayed on the user's home screen, all harmless but very annoying.
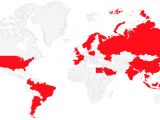
Currently, the adware has been found on Android versions ranging from 2.3.4 to 5.1.1. with the most infected users in countries like Russia, China, Brazil, Argentina, Egypt, Spain, France, Germany, Sweden, Norway, Saudi Arabia, Indonesia, India, the UK, and the US.
The NGE adware campaign was first observed in August and has grown at a constant pace ever since.
The adware can be hijacked to deliver more dangerous malware
What's even worse, as FireEye researchers point out, is that the adware's creators were extremely careless when they put together the malicious code.
Because the C&C server communications are carried out via blind HTTP channels, a second attacker could easily intercept these transmissions.
Since the adware gains root privileges and boot persistence over all infected devices, another attacker could use this to serve much more dangerous apps compared to silly adult apps and ads.
The first example that comes to mind is when the second attacker adds infected phones to a botnet and uses them to carry out DDOS attacks. Worse scenarios are when attackers decide to go snooping through your private pictures or install ransomware on your phone.
UPDATE: Following further research into the threat, FireEye has dubbed this mobile malware Kemoge. You can read more on FireEye's follow-up blog post.
 14 DAY TRIAL //
14 DAY TRIAL //