Researchers found a backdoor in the kernel code of Allwiner-powered devices. The backdoor is trivial to exploit and grants root access to the entire device.
Allwinner is a Chinese ARM chip vendor that makes the CPU used by a large number of low-cost Android smartphones and tablets. Its CPUs work on a bastard version of the Linux kernel, and the affected Allwinner custom-developed kernel is linux-3.4-sunxi, which is a specially modified Linux kernel that supports the Android operating system on a series of Allwinner chipsets.
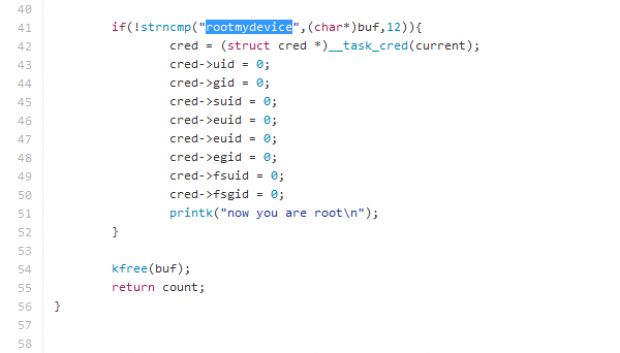
According to the folks managing the Armbian project, an operating system for ARM development boards, the backdoor can be activated just by sending the "rootmydevice" command to a local debug process. This command, in turn, gives the user, or the process, that sent it root privileges. The syntax is:
echo "rootmydevice" > /proc/sunxi_debug/sunxi_debug
Armbian developers claim they've found the backdoor in OS images for H3, A83T or H8-powered devices. Other sources have told Softpedia of discovering the backdoor working on a Pine64 board which uses an Allwinner A64 CPU. Other devices that may use Allwinner CPUs and deploy the linux-3.4-sunxi image may also be affected.
The Armbian team says this is "a network enabled root exploit." A developer who wanted to remain unnamed, also confirmed this for Softpedia.
"So far over the network I was able to push out different commands. Like being able to obtain system information, and even make files ect. Seeing from traffic logs; you can see odd data being transmitted over the network via Bandwidth usage / System monitoring tool like iftop."
Backdoor does not appear to be malicious in nature
In the past, security researchers have discovered similar backdoors in Chinese-manufactured products, such as the firmware for RaySharp and MVPower DVRs.
This does not appear to be the case right now, since the backdoor doesn't seem to be hidden, and all signs point to an Allwinner developer forgetting to remove it from the kernel's source code after debugging operations.
The Armbian team further informed other projects that also deployed the vulnerable kernel code. The list included FriendlyARM, SinoVoip, Cubietruck, and LinkSprite.
@campuscodi haha, they are setting euid to 0 twice! One can never be too sure. — Amit (@0xAmit) May 13, 2016

 14 DAY TRIAL //
14 DAY TRIAL //