Mofang ("to imitate" in Chinese) is the name of a newly discovered cyber-espionage group that targeted various countries around the globe since February 2012, when the group's main malware, called ShimRat, was found by security firm Fox-IT.
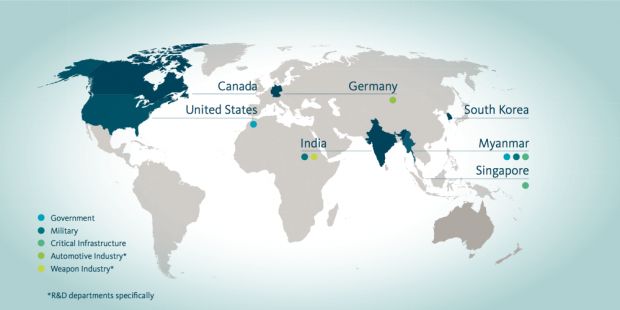
While the first attacks were recorded in February, the group sprang to life in May, when attacks with ShimRat intensified, first targeting the Ministry of Commerce in Myanmar, and then two German companies in the automotive industry.
The group has mainly targeted the Myanmar government
Attacks continued in January 2013, when Mofang hit a Canadian organization, then in April and August 2013, against unknown organizations. The group finished 2013 on a high note in September when they hit a US government agency, and companies in India and Singapore.
2014 was also a busy year, with the group launching attacks in February (South Korean company), April (Myanmar government entity, Canadian and US companies), June (US company), and November (unknown organization).
Attacks continued in 2015 when Mofang hit Myanmar government agencies and private companies in four different incidents.
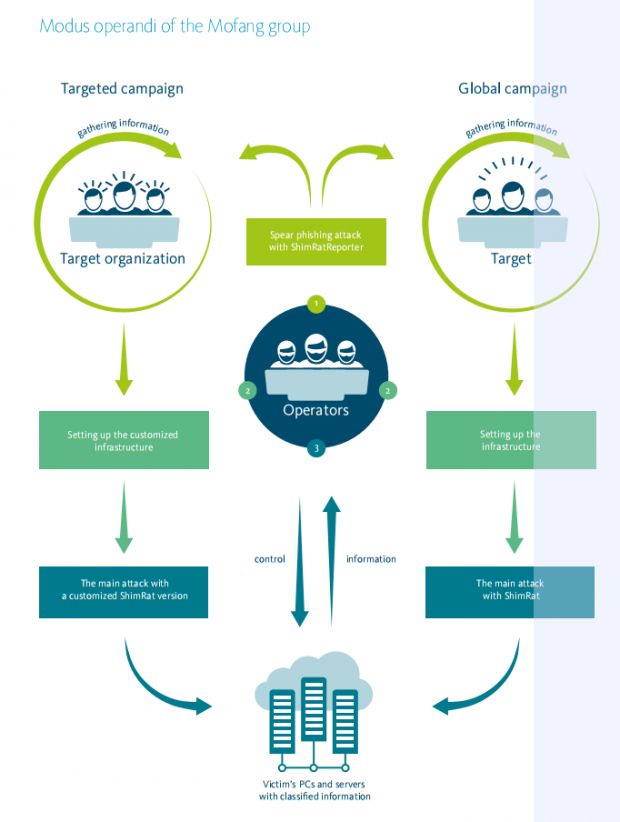
Mofang has a unique mode of operation
Compared to other APTs, Mofang has a distinct mode of operation. The group doesn't rely on exploits to infect a target's computers, but only uses social engineering, mainly via a careful target selection and specifically crafted spear-phishing emails.
Once the group compromises a target, it first carries out reconnaissance, mapping the local network and searching for data worth stealing.
Mofang then deploys faux infrastructure on infected targets, usually in the form of tainted security software, which at a later stage help the group deliver its malware payload, the ShimRat remote access trojan.
The ShimRat malware
In a simpler explanation of the entire Mofang MO, the group sends spear-phishing emails that contain Word, PDF or Excel files. If targets open these files, then executables for legitimate applications are dropped and executed on their computers.
These are legitimate apps, usually from companies such as McAfee, Symantec or Norman. Mofang uses DLL hijacking to disguise its malware within these apps.
At a later stage, these apps drop the ShimRat or ShimRatReporter malware. These two leverage a UAC bypass to escalate their privileges in order to run undisturbed on infected systems.
Because Mofang uses DLL hijacking, the malware runs from its parent process, which is the legitimate app, usually an antivirus.
ShimRat is a basic remote access trojan and can enumerate connected drives; list, create and modify directories; upload and download files; delete, move, copy and rename files; execute programs; execute commands; and even uninstall itself.
The ShimRatReporter malware
On the other hand, ShimRatReporter is only a malware dropper. The group developed it in 2014 in order to gather information on infected hosts before delivering its final payload.
ShimRatReporter can collect information such as IP address, network info, OS info, a list of active processes, browser and proxy configurations, active user sessions, user accounts, and a list of installed software.
This information is then sent to a C&C server, from where the crooks give the go-ahead for a ShimRat infection.
Chinese attribution
On the matter of attribution, Fox-IT expert Yonathan Klijnsma said that Mofang "almost certainly operates out of China and is probably government-affiliated."
"It is highly likely that Mofang’s targets are selected based on involvement with investments, or technological advances that could be perceived as a threat to the Chinese sphere of influence," he also added.
Fox-IT's report on Mofang's activities details a possible link between the cyber-attacks and the investments of a Chinese state-owned company that bid on an oil and gas pipeline project in Myanmar.
During the selection process, the Myanmar government and the financial consultancy firm selected to choose a project winner suffered multiple cyber-attacks at the hand of Mofang. The Myanmar government eventually awarded the project to the Chinese company.

 14 DAY TRIAL //
14 DAY TRIAL //