A new variant of the Chimera ransomware is combining scareware tactics with regular file encryption operations, threatening users it will publish their personal files online if the ransom is not paid until its deadline.
For the moment, this new campaign is only active in Germany and is targeting users in the enterprise market. Security researchers from Botfrei were the ones who discovered this particular strain of the malware.
According to their findings, the ransomware is distributed via emails sent to victims, which contain a link to a Dropbox Web page. Users visiting this link are infected with the Chimera ransomware.
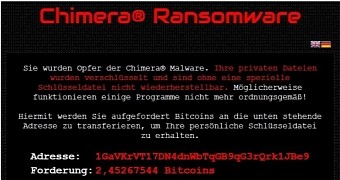
Users who have the unfortunate fate of clicking the Dropbox link and catching a dose of Chimera have their files encrypted and are asked to pay a ransom of 2.45 Bitcoin ($694 / €630) to have their files back.
These are all normal operations, if you’ve ever read about how ransomware infections go. The twist comes that, besides encrypting files and holding them to ransom until a payment is made, Chimera also shows a message that warns users that, if they don't pay up, their data will be published online.
Security researchers: an empty threat
Botfrei researchers said this is an empty threat. "There is so far no evidence or information whether the criminals have stolen [data] from affected systems or that personal information is already published on the Internet," add the researchers (translated).
While, technically, ransomware authors could devise a way to steal data and then upload it online, this is quite an unpractical scenario since this also increases the number of clues they leave behind online, a trail that can easily be followed back to its original source by cyber-crime investigation agencies.
By the way ransomware is constructed to work, publishing files online is not an option, due to the storage capabilities criminals would need, or because this would also increase the amount of attention their actions would receive.
Ransomware authors only want to get paid, and deploying this scareware tactic is a smart move on their part.
 14 DAY TRIAL //
14 DAY TRIAL //