Two Israeli security firms that took a closer look at the Cerber ransomware operations claim that the criminal group running this complex ransomware service is making around $78,000 per month from their illegal activities, which adds up to around $946,000 per year.
Following a lengthy investigation, the two companies, Check Point and IntSights, put together a technical report that offers an in-depth look at how the Cerber operation runs.
As a side effect of their efforts put into this task, the two even managed to create a Cerber decrypter that can help victims unlock files for free.
Cerber run as a RaaS service
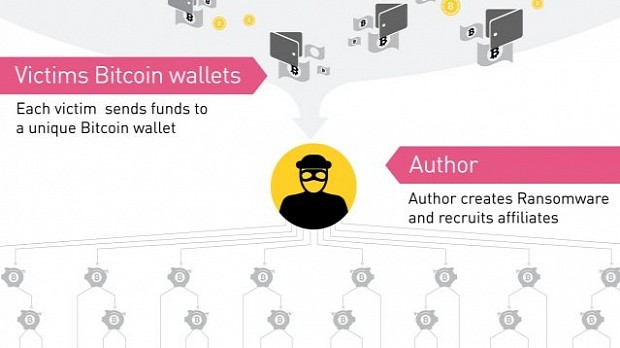
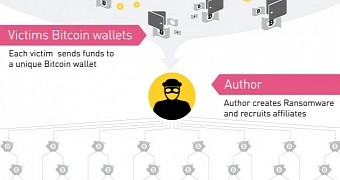
On the technical side of things, the people who developed Cerber opted to go for a RaaS model, a Ransomware-as-a-Service business that rents out the final ransomware payload to other crooks (called affiliates) who take it upon themselves to distribute it to victims.
This operational model is nothing groundbreaking and has been used by many other crooks who developed ransomware in the past, among whom the people behind the Chimera and Petya ransomware variants.
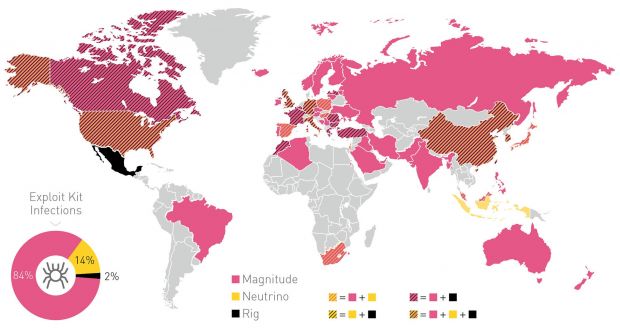
In most cases, Check Point has discovered that Cerber's distribution model involved the usage of exploit kits.
For most distribution campaigns, the affiliates relied on the Magnitude exploit kit (EK), which accounted for 84 percent of all Cerber EK-based infections. Other exploit kits were also used, like Neutrino (14 percent) ad RIG (2 percent), but to a smaller degree.
The two companies didn't only focus on how Cerber gets from the crooks to the infected users, but also tracked down how the money makes its way back to the crooks.
Cerber infections ask for 1 Bitcoin (~$580). Check Point says that all these ransom fees are paid to a Bitcoin wallet under the original Cerber developer's control, who then takes it upon themselves to spread the money to the affiliates responsible for the infections.
Cerber made over 150,000 victims in July 2016 alone
According to Check Point, Cerber, which is today's most active ransomware family, made over 150,000 infections in 201 countries and during 161 campaigns in the past month alone.
By tracking these infections and the payments to the central Bitcoin wallet, Check Point estimates the RaaS service made $195,000 in July 2016 alone.
Of these, the Cerber authors kept 40 percent, which was $78,000, and the rest was spread among the affiliates that helped distribute the ransomware.
This is considerably a higher percentage than what other ransomware services ask. A recent service that came to light yesterday, the Shark Ransomware Project, kept only 20 percent.
"The highly profitable business of ransomware is no longer reserved only for skilled attackers," the Check Point team concludes in its report. "Even the most novice hacker can easily reach out in closed forums to obtain an undetected ransomware variant and the designated set of command and control (C&C) infrastructure servers required to easily manage a successful ransomware campaign."
You can get the full 60-page CerberRing: Ransomware’s Underworld report from here while Check Point's Cerber decrypter can be found here. Check Point claims this decrypted works with both Cerber versions, 1.x and 2.x. Below is a video from GrujaRS showing the new Cerber decrypter in action.
 14 DAY TRIAL //
14 DAY TRIAL //