We reported last week that Canonical has started offering live kernel patch services for users of the Ubuntu 16.04 LTS (Xenial Xerus) operating system running a 64-bit version of the OS and Linux kernel 4.4 LTS.
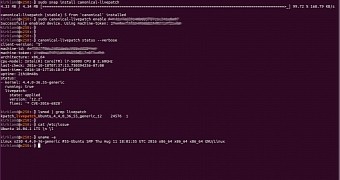
And it now looks like the first Kernel Live Patch Security Notice was published by Canonical's Luis Henriques this past weekend, informing Ubuntu 16.04 LTS users that a couple of security issues are affecting the "generic" and "low-latency" 64-bit kernels of the Xenial Xerus release and its official derivatives.
The first Linux kernel vulnerability patched in this kernel patch is the infamous "Dirty COW" bug (CVE-2016-5195), a race condition discovered in Linux kernel's memory manager when handling copy-on-write breakage of read-only memory mappings, which could have allowed a local attacker to gain administrative privileges (root access).
Ubuntu 16.04 LTS users using kernel live patch need to update to version 13.3
The second kernel vulnerability patched is an unbounded recursion (CVE-2016-7039 and CVE-2016-8666) discovered by Vladimír Beneš in Linux kernel's VLAN and TEB Generic Receive Offload (GRO) processing implementations, which could have allowed a remote attacker to cause a stack corruption and crash the affected system via a denial of service.
Version 13.3 of the live kernel patch is now available for all Ubuntu 16.04 LTS (Xenial Xerus) users running Canonical's new kernel live patch service, which is offered for free for up to three systems, bringing the linux-4.4.0-43.63 kernel update. Please note that you don't need to reboot your system after applying the new version, but Canonical recommends you to also install an updated kernel with these fixes and reboot at your earliest convenience.
 14 DAY TRIAL //
14 DAY TRIAL //