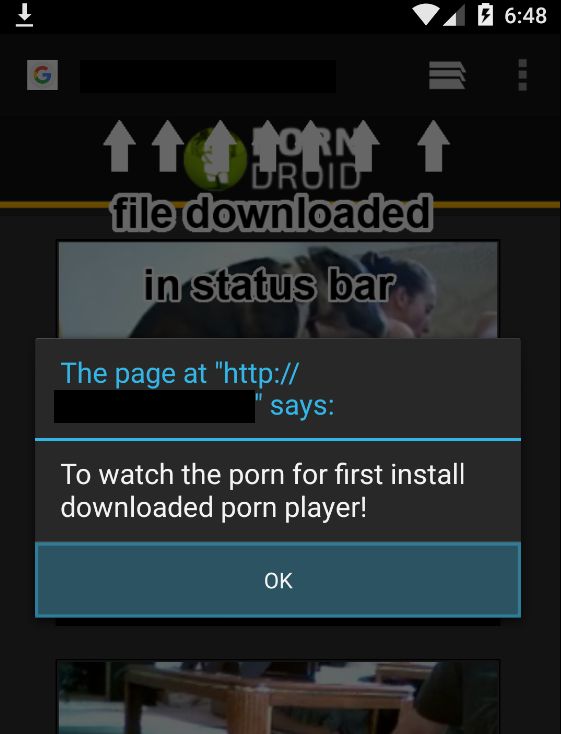
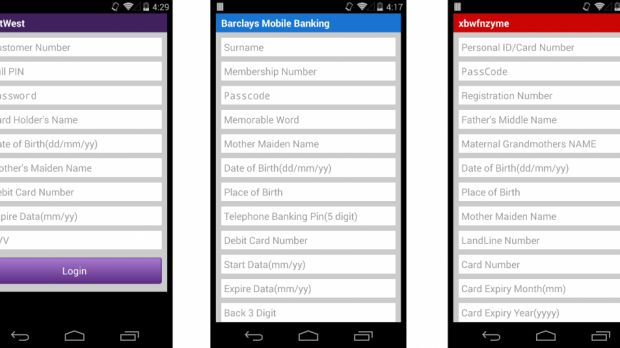
SpyLocker is the name given by Intel Security (McAfee) researchers to a new variant of Android malware that shows credential phishing popups for customers of EU banks and some popular Android applications.
The trojan was actually spotted in a previous campaign a while back, during which it disguised itself as a Flash Player app for Android users, distributed via websites with adult material. The initial attack targeted the customers of banks in Australia, New Zealand, and Turkey.
Intel Security researchers are now reporting on a new wave of attacks, which distribute the same fake Flash for Android app, or sometimes a fake Android system update app, in order to infect users. The difference, this time, is that, besides their own servers, crooks are also utilizing hacked WordPress and Joomla sites.
Banking trojan is somewhat similar to a two-year-old ransomware variant
According to the security firm's experts, the newly discovered banking trojan is somewhat similar to an Android ransomware variant that was active in 2014, called Police Locker. The similarities are few, but they are there nonetheless.
Intel Security says this new SpyLocker campaign only targets the customers of banks in France, Poland, and the UK. Additionally, the company also explains it discovered the necessary modules to target Russian banks, but the crooks did not appear to be interested in doing so.
Besides showing classic popups with bank login forms for various mobile banking apps created by different financial institutions, SpyLocker also targets some popular apps and services such as Google accounts, eBay or Instagram.
SpyLocker now targets only European bank customers
Once the trojan collects the desired data, it sends it to a C&C server, along with other details about the infected device. Further, SpyLocker can also intercept incoming SMS messages, access the call history, check a list of installed apps, and more. Practically all the same things that other modern Android banking trojans can do, of which SpyLocker seems to be a carbon copy.
SpyLocker's malicious functionality is powered by its ability to attain administrator privileges. If users avoid granting such rights to apps they've downloaded from a suspicious website, then most of them should be safe.
Another recently discovered and interesting Android malware variant is Android.SmsSpy, which blended ransomware and banking trojan features, detected by Dr.Web last week, and targeting only Russian users.
 14 DAY TRIAL //
14 DAY TRIAL //