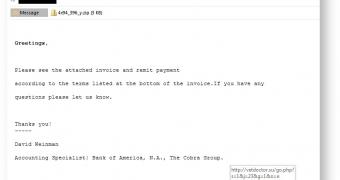
Security researchers from Forcepoint have shed light on a new method of distributing the Cerber ransomware that involves spamming users with unwanted emails that contain double-zipped file attachments.
These emails use the classic "unpaid invoice" trick to lure victims into taking a look at the files. The crooks are even embedding an "Unsubscribe" link into the email's body, to make the emails more convincing. Of course, clicking this link triggers the download of another infected ZIP file.
The second clever trick the crooks used was to double-zip their malicious payload. The reason behind this is to fool basic antivirus scanners that only decompress and look inside ZIP files at the first level. A human user will always unzip all archives, and that's what the crooks are counting on.
Once the second ZIP file decompressed, users will see a Windows Script File (WSF), a special format that automatically runs JavaScript, JScript or VBScript inside ActiveX objects.
Forcepoint researchers claim that crooks are using WSF files to download and install the Cerber crypto-ransomware, first spotted at the start of the year.
Cerber distributed via a RaaS service?
Since its discovery, security researchers have seen this ransomware spread via malvertising and exploit kits on The Pirate Bay, via another set of exploit kits that leveraged the CVE-2016-1019 Flash zero-day, and most recently via weaponized RTF files.
Because of the diverse methods in which crooks are spreading this threat, Forcepoint researchers claim that Cerber is distributed as a RaaS service.
RaaS stands for Ransomware-as-a-Service and is a popular method through which malware coders outsource the distribution of their malicious payloads to specialized cybercrime groups, and then split the profits.
Forcepoint believes that this diverse set of distribution methods hints at the presence of multiple groups delivering Cerber in their own unique way. Furthermore, Forcepoint also believes to have found a way to partially recover some of the files encrypted by Cerber.
"After an in-depth analysis of Cerber we have determined that there are some weaknesses in the encryption implementation which would allow for partial file recovery," the company wrote on its blog. "We are sharing our research privately with a small number of trusted partners and do not intend on releasing this information publicly."
 14 DAY TRIAL //
14 DAY TRIAL //