The EZDATA analytics service used by some major sites is putting users at risk of reflected cross-site scripting (XSS) attacks, according to recent findings by security researcher Ashar Javed.
We're well-aware of Mr. Javed's work in the field of online security, having previously covered the discovery of an XSS bug in YouTube Gaming. His work doesn't stop there, though, Mr. Javed contributing with numerous security disclosures to services like Adobe, Facebook, Microsoft, Google, Yahoo, Twitter, eBay, Etsy, and AT&T.
In his most recent discovery, Mr. Javed came across a common piece of analytics code that various sites from the Alexa 1000 were deploying in their code.
The particular snippet belonged to EZDATA, an analytics service that Mr. Javed, despite numerous efforts, could not get in touch with.
Buggy analytics code leads to reflected XSS exploits
All the sites that loaded the EZDATA analytics were vulnerable via their search field. Passing classic XSS attack vectors did not work since the service included protection against common cross-site scripting techniques, sanitizing user input for problematic characters like (, ), and <.
But as the Web development evolved this year with the release of ECMAScript 6, the latest standard version for the JavaScript programming language, new features are also now present in browsers that open new attack vectors.
One of these is the ECMAScript feature called multi-line template strings, which allows developers to execute code without using parenthesis, using the back-tick character ` instead. This allowed Mr. Javed to craft a malicious string in the form of:
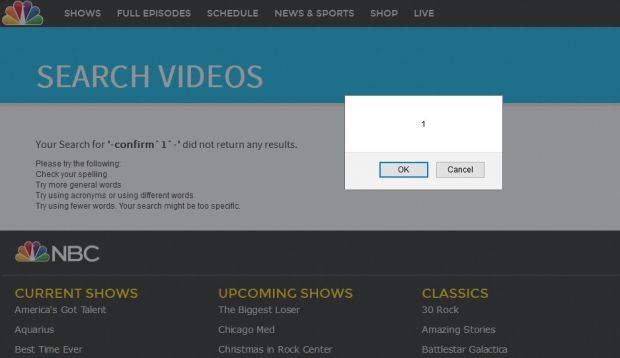
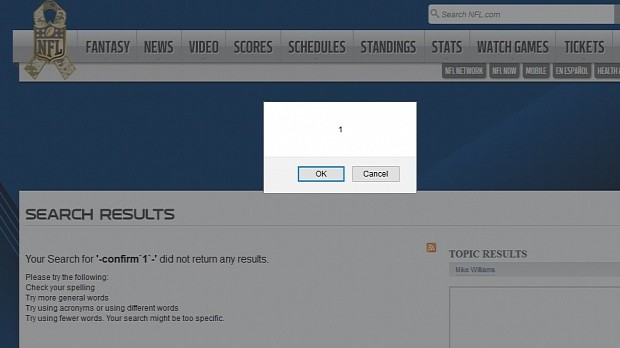
http://sitename.com/search?query='-confirm`1`-'
Replacing the classic confirm command with something more dangerous would put users at risk of more dangerous actions that could harm their browser and expose private information to attacks.
The only condition is that attackers fool the user into clicking such malformed links, which should not be that difficult.
Taking into account that it's the middle of the NFL American football season and that two of the affected sites are NBC.com and NFL.com, two places where football fans go for news and game videos, exploiting the current interest in NFL news could provide cybercriminals with a broad attack target.
For a list of sites that are currently plagued by this XSS issue, please consult Mr. Javed's Blogspot.
 14 DAY TRIAL //
14 DAY TRIAL //