Members of TeamXRat, a hacking crew based in Brazil, have created their own ransomware variant that they spread to local companies and hospitals after taking control over their servers and networks via RDP (Remote Desktop Protocol) brute-force attacks.
The group, who has previously created and sold banking malware, is at its first attempt at creating ransomware, which, based on a Kaspersky Lab analysis, seems to be derived from the Xorist ransomware, detected and decrypted back in March.
Researchers say the ransomware is crude, since it doesn't work with a TOR-based payment site, asks users to contact the crooks via email, and needs manual installation.
TeamXRat hacks into servers via unprotected RDP services
To achieve a position from where they can install their malware, the crooks carry out brute-force attacks against Internet-exposed RDP servers found at Brazilian companies and state institutions.
RDP is a protocol often employed at larger companies to allow sysadmins to log in and manage remote workstations. Most of the times, they are exposed to the Internet, not only the company's Intranet, and sometimes use weak, easy-to-break passwords.
Kaspersky says it was alerted to the existence of this new ransomware variant after an unnamed Brazilian hospital has asked the company for help in unlocking their files.
Xpan ransomware can be decrypted
The ransomware, which is detected as Trojan-Ransom.Win32.Xpan, uses dual AES-256 CBC and RSA-2048 encryption to lock files, but Kaspersky said it identified weaknesses in its encryption that allowed its staff to create a decrypter. Victims who need this decrypter should contact Kaspersky via their support section.
The rest of Xpan's behavior is similar to most other ransomware variants. Xpan locks the user's files, changes his wallpaper, asks for 1 Bitcoin (~$600) ransom, and adds a registry key that opens a custom ransom note every time the user tries to open an encrypted file.
Xpan victims can detect an infection based on the custom file extension the ransomware appends to all locked files: .____xratteamLucked.
TeamXRat is not the first Brazilian-based crew to try its hand at ransomware. In the past, security firms have detected TorLocker and numerous ransomware families based on the Hidden Tear open source ransomware starter kit. The Brazilian malware scene is generally known for boleto spam and a flourishing banking trojan scene.
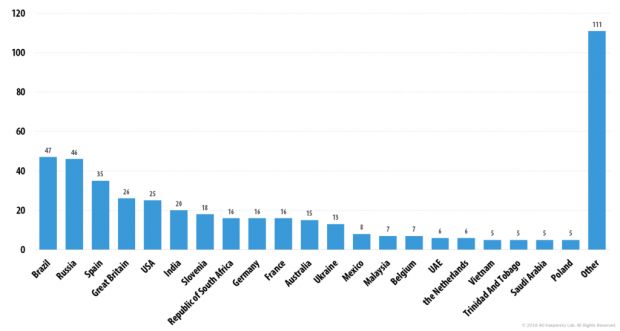
In June, when Kaspersky revealed the existence of xDedic, a marketplace for selling compromised servers, Brazil was the country with the most hacked RDP servers.

 14 DAY TRIAL //
14 DAY TRIAL //