Italian security researchers from VoidSec have come across a botnet structure that was using vulnerable Aethra Internet routers and modems to launch brute-force attacks on WordPress websites.
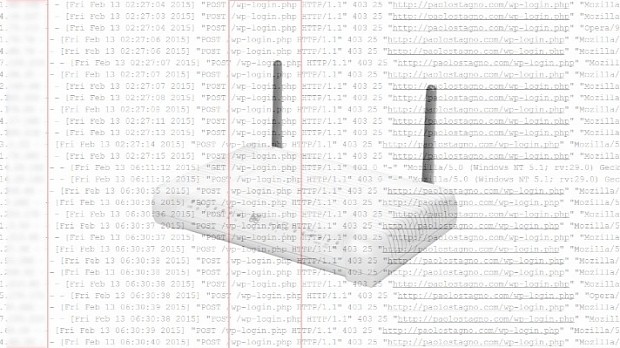
This particular incident was uncovered after one of the VoidSec researchers was sifting through his WordPress log file and found a brute-force attack coming from the same IP range.
After further investigation, all the IPs came from six Internet Service Providers (ISP): Fastweb, Albacom (BT-Italia), Clouditalia, Qcom, WIND, and BSI Assurance UK, four of which are from Italy.
What all these networks had in common were Aethra routers. VoidSec researchers narrowed down most of the attacks to these devices.
Hacker's best friend: Internet router with no admin password
Further inquiry into these routers showed that all were still using their default credentials. This made them very easy to take over by attackers, since both the default admin username and passwords were non-existent (blank spaces).
Additional investigation also revealed that some of the routers were also susceptible to various reflected XSS and CSRF attacks that would also allow attackers to take control of the device, even if using different login credentials.
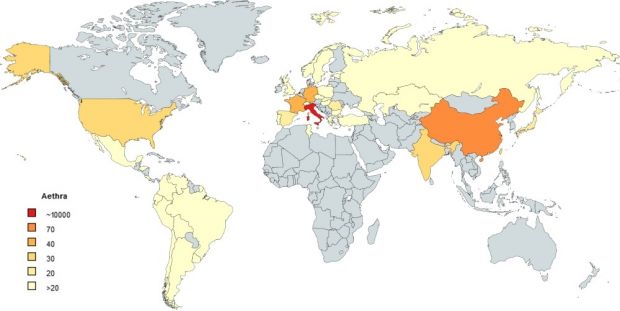
Using Shodan, a search engine for locating Internet-connected devices, researchers found over 12,000 of Aethra routers around the world, 10,866 in Italy alone, and over 8,000 of these devices were of the model detected in the initial brute-force attack (Aethra Telecommunications PBX series). At that time, 70% of these Aethra routers were still using their default login credentials
According to a rough estimate, based on the average bandwidth associated with each router's ISPs, each infected router would be able to send out traffic between 1 and 10 Gbps during a DDoS attack.
Public disclosure: One ISP quickly patches, the other goes silent for 11 months
VoidSec contacted two of the main Italian ISPs abused by this botnet, Fastweb and BT-Italia.
Fastweb was quick to react, and in seven business days issued firmware updates for all affected Aethra routers, since the company was using a custom firmware and not the one that came from the manufacturer.
On the other hand, BT-Italia acknowledged the issue but then ceased any communications with the security researcher for more than 11 months. Its Aethra routers are still vulnerable, VoidSec confirms, after going public with their findings.
 14 DAY TRIAL //
14 DAY TRIAL //