A hacker that calls himself DetoxRansome has managed to crack the defenses of one of Bitdefender's servers and steal user login credentials.
In a statement for Softpedia, the company confirmed the breach, but stated that no more that 1% of its SMB user accounts were leaked.
Bitdefender also said the database was storing the login credentials of only small to medium business accounts, which were reset in the meantime, and no home or enterprise clients were exposed.
A human error was at the core of the breach
According to the internal investigation that followed the incident, it was found out that only one server was affected, made vulnerable by a human error during its deployment, as PCWorld notes.
After acquiring the Bitdefender data, DetoxRansome tried to blackmail the company into paying $15,000 / €13,600, otherwise he would release the data (as seen in the tweets embedded at the end of the article).
The hacker also posted a few accounts and their passwords in several tweets, and 250 more inside a Pastee URL (website that anonymously hosts text files).
According to Hacker Film Blog, "Travis Doering and Bitdefender were able to confirm many of them as active accounts."
The Bitdefender data was up for sale for 8 Bitcoin
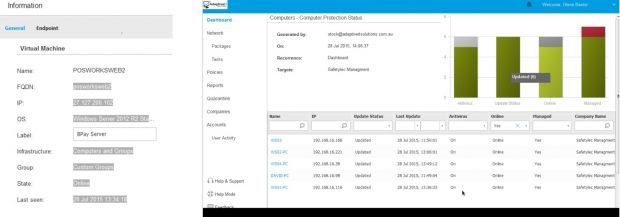
Contacted by email, the hacker agreed to sell the data for 8 Bitcoin, and as proof, provided a screenshot of the Bitdefender dashboard for the posworks.com.au account (see below).
DetoxRansome detailed his intrusion method as "sniffing one of their major servers [and] stealing logins."
In an email sent to Forbes, the hacker also claims the passwords were stored in clear text, and put the blame on Amazon's Elastic Web cloud, "which is notorious for SSL problems."
This was not the first time this year an antivirus company was under attack, as earlier in June, Kaspersky Labs also suffered a breach when the Duqu group penetrated some of its internal systems using a zero-day in the Windows Kernel.
You can read the full official BitDefender statement below:
We recently found a potential security issue with a single server. We immediately launched an investigation and found that a single application was concerned – a component of the public cloud – exposing a very limited number of usernames and passwords.
Our investigation also revealed that the server was not penetrated, but a vulnerability potentially enabled exposure of a few user accounts and passwords.
The issue was immediately resolved and, additional security measures were put in place in order to prevent it from reoccurring. As an extra precaution, a password reset notice was sent to all potentially affected customers, representing less than 1% of our SMB customers. This does not affect our consumer or enterprise customers. Our investigation revealed no other server or services were impacted.
Bitdefender takes security of its customers very seriously and any issue that might involve the security of our customers or the security of our servers is treated with the utmost urgency and seriousness
@bitdefender i want 15,000 us dollars or i leak your customer base
— tartarus_destroyer (@detoxransome) July 24, 2015
@bitdefender back to earth [email protected]:Shr1h@r1 [email protected]:w_P~GK@C3N [email protected]:Mudei123@
— tartarus_destroyer (@detoxransome) July 26, 2015

 14 DAY TRIAL //
14 DAY TRIAL //