A connection may exist between an Internet-accessible unprotected MongoDB database and the theft of funds from the Bitcoin wallets of several clients of the Coinroll Bitcoin casino.
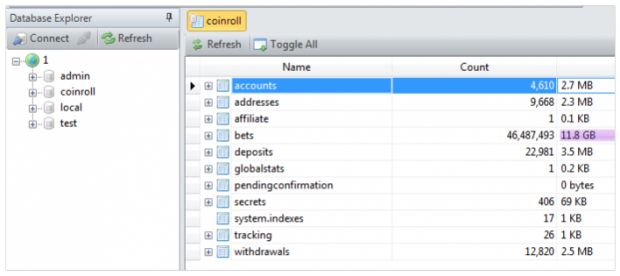
On March 30, MacKeeper security researcher Chris Vickery says he discovered a MongoDB database holding sensitive information about the customers of Coinroll, a website where users can register and bet small amounts of Bitcoin on the roll of a dice.
Besides being freely available for anyone over the Internet, the database also didn't have an administrative password, meaning any snooping user could have downloaded its content.
Passwords were hashed, but not salted
Mr. Vickery says he discovered 4,610 Coinroll user accounts, tied to 9,668 Bitcoin wallets, which he reported to Coinroll's staff.
The problem that Mr. Vicker identified was that the database also exposed the passwords for each account. While all password strings were hashed using a strong SHA256 cryptographic algorithm, they were not salted, which is the process of adding random data to each SHA256 hash, making them near impossible to crack.
This meant that if an attacker got hold of the data, they could compare the SHA256 hashes of common password strings and identify accounts and wallets with weak credentials.
The researcher didn't have to wait long for a response from Coinroll, who answered the next day.
Coinroll admits its security lapse, reveals mysterious thefts
"Well the admins are working on issues," Coinroll Marketing & Affiliate Manager Juan-Samuel Codina-Fauteux wrote back. "There had been reports of some users getting their [casino account] balance stolen. Another possible vulnerability was suspected, although nothing definitive. A few users had already been refunded."
Mr. Codina-Fauteux also said that the exposed database was a side effect of a recent Ubuntu update that altered some UWF rules. UFW is a firewall configuration tool for iptables that is included with Ubuntu.
This technical error contributed to the database being accessible via the Internet. Coinroll's IT staff also admitted to their own mistake when they said they forgot to set a MongoDB admin password.
A possible and believable link exists between the two incidents
The company said they intend to move from Ubuntu to Fedora in the upcoming future so that these update issues wouldn't happen again.
"I believe that the most likely scenario behind any heist of Coinroll Bitcoins is one of two possibilities," Mr. Vickery speculated. "Either (1) someone else found that exposed database before I did and compared the sha256 hashes to common passwords; or (2) someone else found the database and used the knowledge of its structure to successfully manipulate login data via MongoDB injection attacks."
Coinroll followed through with their security audit, and on April 11, they posted the following message on its website.
 14 DAY TRIAL //
14 DAY TRIAL //