Security researchers from Symantec are sounding the alarm on an unknown Android feature that was shyly abused this past fall to install adware, but which they say can also be employed to deliver more dangerous threats.
This glaring security hole exists in the Android operating system and takes the form of the device's Accessibility service, a feature that lets users with various disabilities interact with their smartphones.
Social engineering is needed to trick users into activating the feature
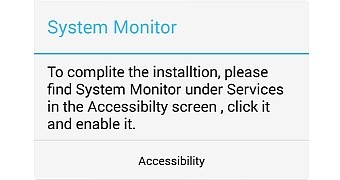
The first signs of crooks abusing Android's Accessibility feature arose last fall, when the Shedun (GhostPush) malware used it to deliver adware and PUAs (Potentially Unwanted Apps) to devices in China and South-East Asia.
Crooks were telling users during an app's installation process that the application needed access to the device's Accessibility feature and that they should turn it on.
In cases where users granted access to this feature, the malware would abuse the Accessibility service's automation features and broad APIs to execute actions in the user's name and query for sensitive data that they couldn't via Android's regular APIs.
Only used by adware until now
Symantec researchers say that one such query is the one that tells developers which is the current app running in the foreground. This query is of extreme importance for malware developers because it allows them to detect the user's currently running app and show ads on top of it.
Security researchers claim that it's only a matter of time until crooks may start utilizing the Android Accessibility feature to query for foreground apps and then use these results in mobile banking malware, not just adware.
While adware is merely annoying because it only shows ads on top of your apps, banking malware may use the Accessibility feature to know when you're using your banking app, and show fake screens on top, harvesting your login credentials.
The Accessibility feature is a newer alternative to older Android tricks
Current banking malware rarely works in recent versions of Android because most of them use the getRunningTasks() function to detect apps running in the foreground. Because of this abuse, Google blocked the function starting with Android 5.0 (Lollipop).
Using the Accessibility workaround, malware coders could very easily port their code to work on newer Android versions, on and past Lollipop. The only downside of using this trick is that users still need to manually turn on the Accessibility feature.
Nevertheless, installing Android malware, in general, is a social engineering trick, so if a crook manages to trick a user into installing shady apps on their device, it's obvious the victim will be willing to turn on the Accessibility service as well.
Symantec has also revealed that the most recent Android adware families it detected abusing the Accessibility service are Android.Generisk and Android.Malapp.
 14 DAY TRIAL //
14 DAY TRIAL //