No sane company would ever think of deploying a backdoor in its hardware products, so that's why Arris, a cable modem manufacturer, decided to add two, just to be sure one of them was working.
Bernardo Rodrigues, a Brazilian security researcher, found this particular issue, affecting old models of cable modems sold by Arris (TG862A, TG862G, DG860A).
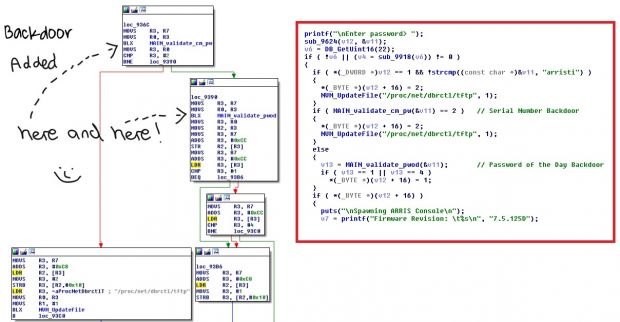
As Rodrigues explains inside his much more technically detailed blog post, the Arris cable modems have a backdoor in their firmware, which, in turn, is affected by another backdoor.
The first backdoor is activated via the libarris_password.so library that gets loaded on the modem, allowing privileged account logins using a custom password, different for each day of the year. This backdoor has already been known, having been discovered in 2009 but never fixed.
When users or attackers exploit this backdoor, they can access the modem and enable SSH or Telnet ports, which, in turn, help them launch a more powerful shell sessions. The user "root" and password "arris" are sufficient to access this shell.
Nested backdoors, just because...
Rodrigues analyzed this backdoor's code in more depth and found inside it another backdoor (backdoor in the backdoor), which launched a BusyBox shell.
BusyBox is a software package that provides various UNIX utilities inside one single executable file. BusyBox is usually used on embedded devices where memory and storage restrictions cannot allow a more powerful Linux OS to run.
Rodrigues found out that the password for this hidden BusyBox shell is based on the device's serial number. He later created a tool to automatically generate this password.
According to Shodan, over 600,000 of such modems are still easily accessible online. Arris told Rodrigues they planned on issuing a fix, but the researcher published his findings after waiting for over 65 days for a patch to be disclosed.
"I'm pretty sure bad guys had been exploiting flaws on these devices for some time (just search for ARRIS DNS on Twitter, for example)," says Rodrigues.
The security researcher made a proof-of-concept video (below) but still plans to withhold the complete exploit code until the vendor fixes its issues.
UPDATE: Mr. Rodrigues has informed Softpedia that Arris modems actually have 3 backdoors, with details about the third being on the ConsoleCowboys Blog.

 14 DAY TRIAL //
14 DAY TRIAL //