In just one week back in February this year, Akamai's security products picked up automated attacks that employed over one million different IPs to test login credentials and hijack user accounts.
Akamai says the crooks employed 1,127,818 different IPs to launch 744,361,093 login attempts using 220,758,340 distinct email addresses.
Attackers targeted multiple services, but a vast majority of the login attempts were aimed at two companies, one in the financial sector, and the other in media & entertainment.
Crooks tried to gain access to accounts at a company in the financial sector
The automated attack against the financial target accounted for over 90 percent of the total attack volume.
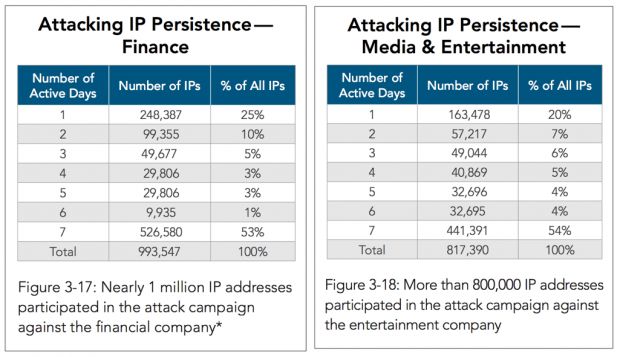
Akamai says crooks used 993,547 distinct IPs to check 427,444,261 accounts. The security and networking giant was alerted to the presence of this campaign because 22,555 IPs had been previously blacklisted by their WAF (Web Application Firewall).
The campaign against the financial institution started strong, with the attackers checking over 248,000 IPs on the first day, and ended even stronger with the attackers testing more than 526,000 IPs on the seventh day, which accounted for more than half of the total IPs used in the attack.
Similar attack targeted a media & entertainment company
In the same week, crooks also launched a similar account takeover attack against a media & entertainment company. Akamai claims it detected 817,390 distinct IPs that launched 388,674,528 login attempts using 65,556,491 email addresses.
This attack followed the pattern of the first, showing a strong start and a stronger finish, with crooks using more than half of their total IPs on the seventh day.
Akamai adds that 778,786 IP addresses, more than 70 percent, were used in both campaigns, leading to the conclusion that the same group was behind the attacks.
Crooks used proxy servers, compromised routers, and cable modems
For these particular campaigns, Akamai experts detail that a large portion of the attacking IPs corresponded to proxy servers, but they also reveal they found a lot of compromised home routers that were also participating in the attacks.
The company specifically mentions the presence of a botnet of compromised ZyXel modems and routers, but also of one made up of Arris cable modems.
Security researchers have found and publicly disclosed at least three different backdoors in Arris cable modems last year, in November.
ATO attacks are becoming more popular
These types of attacks are known to industry experts as ATO (Account TakeOver) (also known as Identity Testing Attacks) and are considered a subset of brute-force attacks.
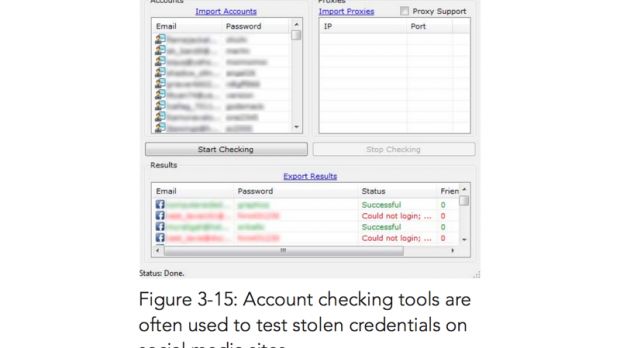
Crooks use public data breaches to collect account credentials from sites like PasteBin to launch their attacks on adjacent services where users might have reused their login details.
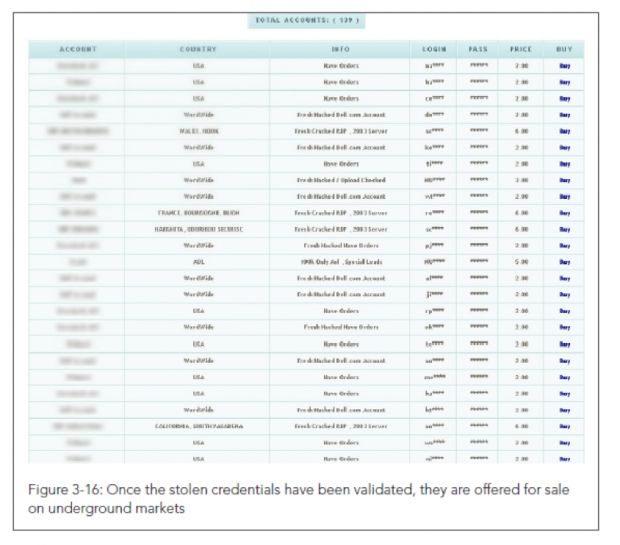
Crooks also buy batches of leaked credentials on underground hacking forums, but they also breach companies themselves via SQL injections and steal account details.
During the past week, GitHub was the victim of a similar ATO attack. The company said attackers managed to gain access to some accounts, which then forced GitHub to reset the passwords for the affected profiles.
 14 DAY TRIAL //
14 DAY TRIAL //