A malformed ping could easily take down your FreeBSD machine if certain conditions are met, and most of them are in standard FreeBSD configurations, researchers from the Positive Research Center have discovered.
All versions of the FreeBSD operating system are affected by a vulnerability (CVE-2016-1879), which resides in how the SCTP (Stream Control Transmission Protocol) is handled.
SCTP is a networking protocol that's often referred to as TCPng, or TCP - Next Generation, built in 2000 on the principles of TCP (created in 1974), but with support for asymmetric communications via the classic IP protocol, along with many other features like encryption support and multihoming.
The Positive Research Center have identified an issue in how this protocol works together with the IPv6 protocol, which is slated to replace IPv4 Internet addressing in a couple of years.
Attackers can use malicious pings to DoS your FreeBSD machine
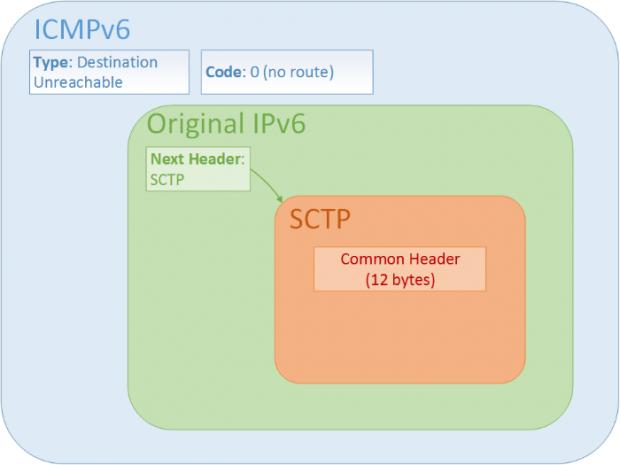
The problem, as depicted in the image below this article, is how SCTP shares header information with IPv6, which then lends it to other protocols like ICMP (Internet Control Message Protocol). ICMP is also an Internet protocol, and we all use it when sending pings between servers to see if they're still up.
According to the research team, if an attacker sends a ping to our FreeBSD box but creates a malicious packet with an SCTP header of a different size than 12 bytes, it offsets values inside the operating system's computations, causing a kernel panic, which resets the machine. This is a DoS (Denial of Service) attack and is often employed with other exploits to break into vulnerable machines.
The Positive Research Center says that all FreeBSD versions that support SCTP, IPv6, and ICMPv6 are vulnerable. These protocols are the default configuration for FreeBSD versions 9.3, 10.1, and 10.2.
The FreeBSD team has done its due diligence, and at the researchers' notification, it has issued patches to address this vulnerability by releasing FreeBSD OS versions 9.3-p33, 10.1-p26, and 10.2-p9.
Since there is no requirement to have an SCTP socket open, there are currently no mitigations for this issue except updating your FreeBSD version. Researchers say that sysadmins could disable IPv6 and SCTP, but that is only a temporary fix since the Web is evolving towards the broad usage of these protocols.
 14 DAY TRIAL //
14 DAY TRIAL //