Crook are spending a lot of time and resources launching brute-force attacks on RDP (Remote Desktop Protocol) servers in an attempt to penetrate corporate networks and spread ransomware to high-value targets.
Remote Desktop is a proprietary protocol designed by Microsoft to allow system administrators to manage Windows computers in remote locations, via LAN or the Internet.
When logging into a remote computer, the user is always asked to authenticate using one of the host accounts and its username and password.
Just like any user authentication system, RDP logins are susceptible to brute-force attacks, during which an attacker tries several different username and password combos in an attempt to guess the correct login.
Real-world attacks detected leveraging RDP
"Day in, day out, failed login attempts are recorded coming from hundreds of unique IP-addresses trying hundreds of unique usernames," says Wouter Jansen, Senior Forensic IT Expert at Fox-IT. "The compromised user account and system could be added to a botnet, used as proxy server, or used for sending out spam e-mail messages. Plenty of possibilities, including taking the company data hostage by executing ransomware."
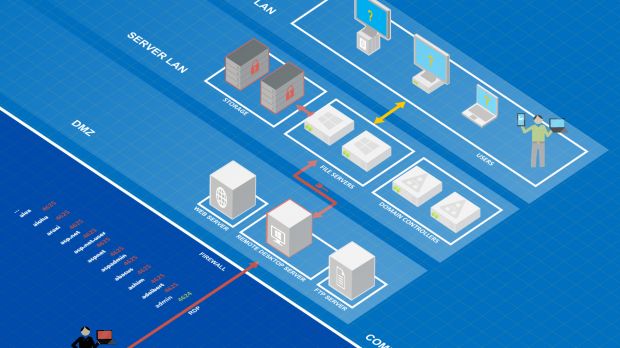
Once an attacker breaches an RDP server, the hacker can use this entry point to spread to other systems on the same network. If the breached server is also a network domain admin, credentials for each client workstation can be harvested and used to break into those PCs as well.
In a recent wave of attacks, Fox-IT experts are saying that ransomware is starting to become a favorite tool for attackers. While in the past hackers used insecure RDP servers to infiltrate networks and steal data, it has now become much easier to monetize attacks via ransomware.
In a series of detected attacks, the crooks are leveraging the central position of RDP servers in a corporate network to spread to as many computers as possible, locking sensitive corporate data and asking for huge sums of money.
Crooks are making a fortune by taking advantage of large corporate networks
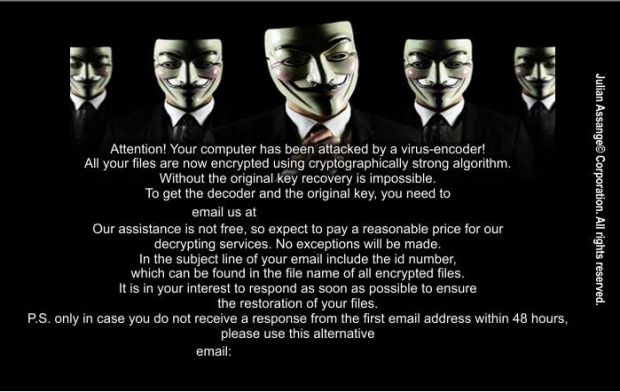
In most cases, the crooks aren't using fixed ransom prices but are only leaving behind an email address, where victims can contact them and negotiate for the decryption key's price, based on the size of their network.
Companies that want to avoid such scenarios should not expose RDP ports unless strictly necessary, and in that case, they should protect connections via firewalls and security solutions that can detect automated brute-force attacks.
 14 DAY TRIAL //
14 DAY TRIAL //