A group going by the name of Armada Collective is still sending extortion emails to website owners around the globe, one year after this type of attack became widely known.
The latest victim of these tactics is Etienne Delport from Port Elizabeth, South Africa, owner of Alpha Bookkeeping Services.
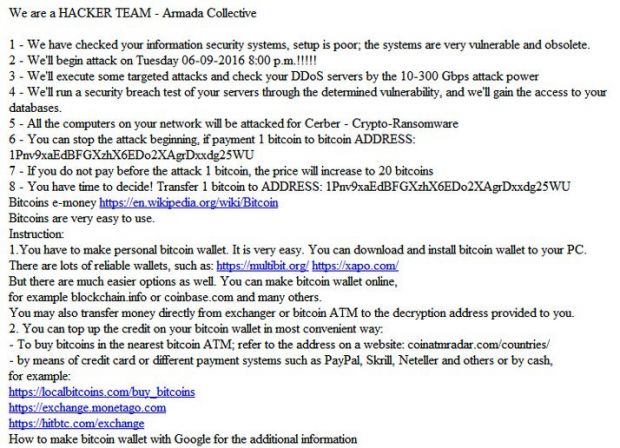
On September 5, Delport published an email on Twitter, showing a ransom note he received from a group claiming to be Armada Collective.
Group claiming to be Armada Collective still lurking around
The group was threatening him with a 10-300 Gbps DDoS attack the next day, unless he paid 1 Bitcoin (~$610) to a certain address. The email, embedded in full below at the bottom of this article, also said the ransom would go to 20 Bitcoin (~$12,150) if the DDoS attacks started, and he wanted the group to stop afterward.
These types of extortion attempts became common last year when a group of hackers using the DD4BC name started employing them.
Europol arrested the group this past winter, but other copycats appeared, including one called Armada Collective, whose most famous attack was against ProtonMail, when they forced the secure email provider to pay $6,000 to stop a massive DDoS attack.
The rise of an armada of Armada Collective copycats
After that event, extortion attempts from the group waned, but in the winter of 2016, many companies started reporting similar DDoS-for-Bitcoin extortion attempts.
Security researchers weren't able to pin any of these attempts on the real Armada Collective group, but their number grew exponentially and started to target any website owner, not just large companies that could afford the ransom.
In April, CloudFlare reported that a group, using a certain list of Bitcoin addresses in its emails, was only threatening to launch DDoS attacks on websites, but they never came through. The group used both the Armada Collective and LizardSquad names in their emails, two hacking crews known for their massive DDoS attacks.
At that point, it was clear that you couldn't distinguish the real Armada Collective ransom emails from the flurry of copycats that spawned following the successful ProtonMail attack from the previous autumn.
Attackers are now threatening to deploy Cerber ransomware
This most recent ransom email that Delport received last week shows the group behind these attacks incorporating a new wrinkle in their tactics.
With all the hype surrounding ransomware infections these days and the ever-growing number of new ransomware families, the group thought it would be a great idea to name-drop the Cerber ransomware in their email.
"All the computers on your network will be attacked for Cerber - Crypto-Ransomware," the extortion email reads.
Reading this, the first impression is that the group members are obviously not native English speakers. The second, they have no idea how Cerber works.
A DDoS attack cannot install ransomware on a network. Web servers are often hosted on Linux machines. Cerber does not support infecting Linux devices. In order to install Cerber on the network, the attackers would need to breach the servers. If an attacker is skilled enough to breach servers and access internal networks, then they'll be probably selling your internal data on the Dark Web instead of bragging about it in an extortion email. The group most likely wanted to issue another threat, to scare victims.
Ransom emails go back for months
In an interview with IBTimes, Delport said he has no plans to pay the ransom. The same report cites a second victim that received this email, Michael O'Connor from Cornwall, UK.
Taking a look at the Bitcoin wallet found in the ransom note, we see that there have been no payments made.
Googling the "1Pnv9xaEdBFGXzhX6EDo2XAgrDxxdg25WU" address, we discover a slew of other people sharing their ransom notes, with the same Bitcoin address, going back to the beginning of the year.
To pay or not to pay?
The Bitcoin address is also the same one found in extortion attempts detected by CloudFlare in April, tied to the group that used both the Armada Collective and LizardSquad names.
In its initial report, CloudFlare claimed that this copy-cat group only launched empty threats. CloudFlare even argued that the group didn't have the technical capabilities to launch DDoS attacks. Nevertheless, when Softpedia published an article about the group, we were under a DDoS attack for at least 12 hours.
If website owners receive such emails, they should use the time between its arrival and the DDoS deadline time to invest in DDoS mitigation services. Law enforcement's position on extortion attempts, regardless of whether they take place in the real world or cyberspace, is to not pay the ransom.
In Delport's case, the attackers never followed through with their threats. Below is the extortion email in text format, embedded in full.
We are a HACKER TEAM - Armada Collective
1 - We have checked your information security systems, setup is poor; the systems are very vulnerable and obsolete.
2 - We'll demonstrate our work in the nearest future, this week. We'll execute some targeted Attacks and check your DDoS servers by the 10-300 Gbps Attack power
3 - We'll run a security breach test of your servers through the determined vulnerability, and we'll gain the access to your databases.
4 - All the computers on your network will be checked for the viruses and malware penetration Cerber, Locky, Cryptolocker - Crypto-Ransomware
5 - We save all the check data, you can get the data before the start of testing
6 - You have time to decide: whether you are going to wait for the start of your security systems testing, or you’d like to get the data before testing?
7 - We can start testing any time, so please, be prepared.
The price for information about security vulnerabilities of your systems is 1 bitcoin to ADDRESS: 1Pnv9xaEdBFGXzhX6EDo2XAgrDxxdg25WU
The price for testing of your systems is 20 bitcoins
Transfer 1 bitcoin to bitcoin ADDRESS: 1Pnv9xaEdBFGXzhX6EDo2XAgrDxxdg25WU
If you do not pay before the Attack 1 bitcoin the price will up to 20 bitcoins
Bitcoins e-money https://en.wikipedia.org/wiki/Bitcoin
Bitcoins are very easy to use.
Instruction:
1.You have to make personal bitcoin wallet. It is very easy. You can download and install bitcoin wallet to your PC. There are lots of reliable wallets, such as: https://multibit.org/ https://xapo.com/
But there are much easier options as well. You can make bitcoin wallet online, for example blockchain.info or coinbase.com and many others.
You may also transfer money directly from exchanger or bitcoin ATM to the decryption address provided to you.
2. You can top up the credit on your bitcoin wallet in most convenient way:
- To buy bitcoins in the nearest bitcoin ATM; refer to the address on a website: coinatmradar.com/countries/
- by means of credit card or different payment systems such as PayPal, Skrill, Neteller and others or by cash, for example:
https://localbitcoins.com/buy_bitcoins
https://exchange.monetago.com
https://hitbtc.com/exchange
Please search how to buy bitcoins, how to make bitcoin wallet with Google for the additional information

 14 DAY TRIAL //
14 DAY TRIAL //