Last week, Agence France-Presse revealed a series of attacks against Hong Kong government officials just ahead of the region's legislative elections that were held during this past weekend. The report cited a FireEye high-ranking exec, who said his company detected attacks against two Hong Kong government departments.
Today, Symantec's security team has released an in-depth account of those attacks, even if they didn't reveal the departments targeted in these recent waves of hacking attempts, which FireEye and Honk Kong government officials said failed.
As FireEye, Symantec identified the group behind the attacks as APT3, referred to by Symantec in its report as Buckeye, but also identified in other reports from security vendors as Gothic Panda, UPS Team, and TG-0110.
APT3 shifted focus from the US to Hong Kong
The group, which most security vendors believe to be operating from China's borders, was historically active against targets in the US and the UK.
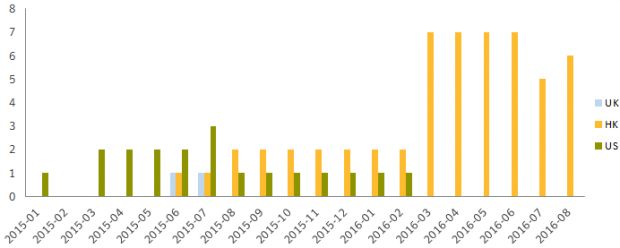
As FireEye initially pointed out and as Symantec also reveals, this group changed its targeting in recent years and migrated operations towards Hong Kong objectives, with August 2015 being the date when this happened.
Symantec says that, starting with 2015, their security products identified at least 82 organizations around the world that were infected with historically linked APT3 hacking tools and malware, such as the Pirpi remote access trojan and various modified open-source tools, for the purpose of their attacks.
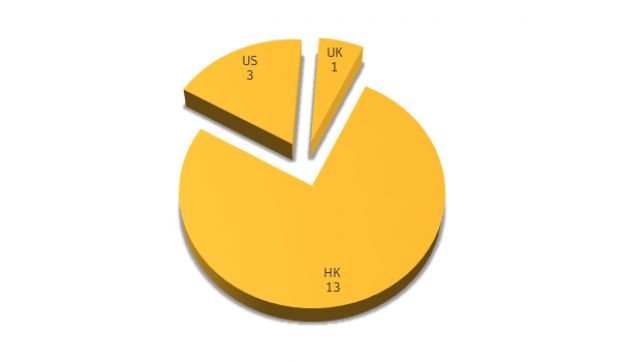
Of these 82 targets, Symantec says that APT3 remained active on only 17 organizations, where they obviously found valuable information. The company says that 13 of these 17 were organizations and individuals from Hong Kong, three were from the US, and one from the UK.
APT3's shift towards Hong Kong targets can also be seen in the graphic below, showing all 82 compromised targets.
According to Symantec, APT3 deployed a true arsenal of hacking tools in order to compromise their targets and exfiltrate desired information.
Symantec's researchers discovered the Pirpi RAT, keyloggers, RemoteCMD (tool for executing commands on remote PCs), PwDumpVariant (password dumper), OSInfo (system information gathering tool), ChromePass (Chrome password dumper), and Lazagne (password dumper that supports browsers, chats, code repos, email clients, and databases).
APT3 is most likely state-sponsored
Some of these tools, such as Pirpi, were created by the group, but some, such as ChromePass and Lazagne, were open source tools, which APT3 adapted to its mode of operation, according to Symantec.
Despite using open source tools, APT3 was observed in the past deploying zero-days such as CVE-2010-3962, CVE-2014-1776, and CVE-2015-3113 in order to compromise targets, so the group's abilities should not be underestimated.
"Buckeye [APT3] seems to target file and print servers, which makes it likely the group is looking to steal documents," Symantec writes in a report released today. "This, coupled with the group’s use of zero-day exploits in the past, customized tools, and the types of organizations being targeted would suggest that Buckeye is a state-sponsored cyberespionage group."

 14 DAY TRIAL //
14 DAY TRIAL //