Dr.Web detected a new mobile banking trojan targeting Android users, one that uses carefully placed fake payment forms to trick users into giving away sensitive financial details.
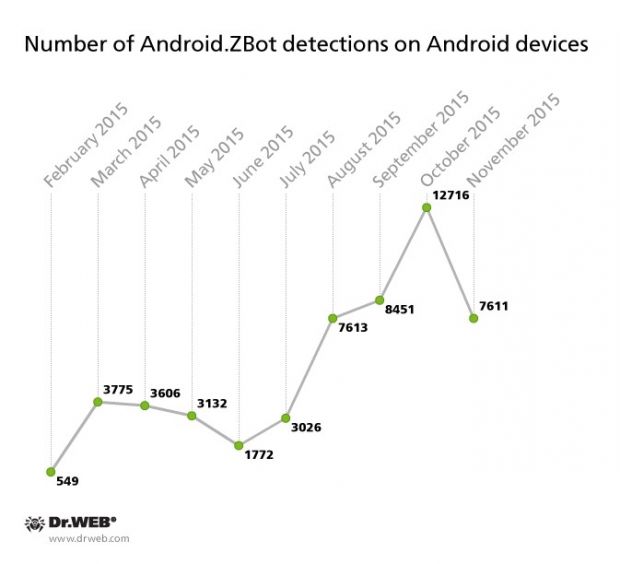
Security researchers detected the trojan (Android.ZBot) for the first time in February, and until now, it seems to have stayed active only in Russia, having infected around 52,000 devices, split across 20 different C&C servers.
Dr.Web's staff claim to have gained access to three of these botnets, where they found between 140 and 2,300 compromised devices. Only 15 of the 20 botnets were still active at the time of Dr.Web's disclosure.
Infections occur via a fake Google Play Store app
Infection, as in most cases, occurs when users are careless enough to install Android apps from unofficial third-party app stores. In Android.ZBot's case, the culprit is an app masquerading as the official Google Play store application.
When this app is installed, it immediately asks for admin permissions. If the user detects the fake and denies it root privileges, the trojan, in a desperate effort, shows a fake payment form on the user's screen, trying to trick them for the last time before being uninstalled. A desperate Hail Mary attempt, but very ineffective.
On the other hand, once the trojan is allowed to install, it hides itself from the home screen, makes sure it starts every time the device boots and starts collecting personal user details.
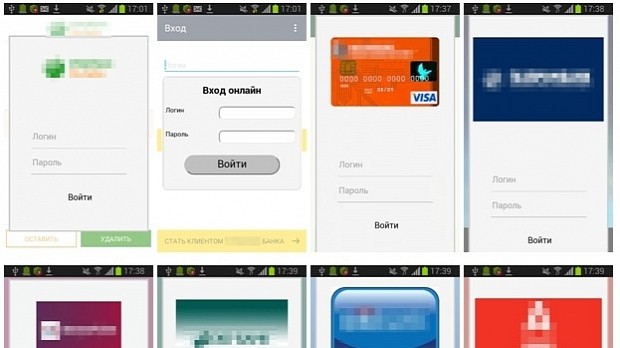
Android.ZBot's main features allow it to watch the smartphone's usage patterns and insert masterfully crafted payment forms inside other apps.
Trojan only targets Russian banking apps, for now
These payment forms mimic the app's native UI and are inserted with the help of the WebView component, a stripped-down browser with no UI.
The trojan doesn't do this to all apps running on the phone, but only to a list of select list, which it constantly retrieves and updates from a C&C server. Most of them are banking or financial-related apps deployed exclusively in Russia.
"Although this is a classic phishing attack, the way it is carried out in this particular case is rather unique," says the Dr.Web team. "Virus makers themselves often label these malicious features as web injections, but, in fact, it is not the case—due to restrictions on Android, Trojans cannot inject an external HTML code into dialog forms of the attacked applications."
Dr.Web researchers also said that pressing the Back button when this fake form pops out also closes the app, an action that helps cement the illusion that this form is actually part of the app itself, fooling the users into entering real credentials or payment data the next time it shows up.
 14 DAY TRIAL //
14 DAY TRIAL //