Security researchers warn that the source code of an Android banking malware was posted online, along with information on how to use it, which means that users of Android devices are very likely to face an increasing number of attacks in the short term.
Security firm Dr. Web reveals that it has already discovered one malware developed with this leaked source code, adding that it’s distributed as popular applications either directly injected in APKs available online or in third-party stores.
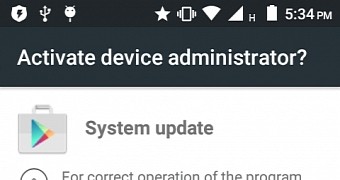
The malware has been flagged as Android.BankBot.149.origin and tries to get administrator privileges on compromised computers. Once it’s granted full privileges, the malware removes the app’s icon from the home screen, trying to trick people into believing it was removed.
Stealing credit card data
But on the other hand, it remains active in the background, and it connects to a command and control server to await for commands. It can perform a wide array of tasks, such as send and intercept SMS messages, steal contacts, track devices, make calls, show phishing dialogs, and steal sensitive information, such as banking details and credit card data.
“Like many other Android bankers, Android.BankBot.149.origin steals confidential user information by tracking the launch of online banking applications and payment system software. One sample examined by Doctor Web security researchers controls over three dozen such programs. Once Android.BankBot.149.origin detects that any of the aforementioned applications have been launched, it loads the relevant phishing input form to access user bank account login and password information and displays it on top of the attacked application,” the firm explains.
Once popular applications are launched, including here Facebook, Instagram, WhatsApp, YouTube, and even the Google Play Store, the malware launches a phishing dialog similar to the one showing up when you make purchases on Google Play, asking for credit card information.
Furthermore, it can intercept text messages, send them to the attacker, and then remove them from the phone, which is particularly dangerous in the case of bank notifications.
The security firm warns that this is just one form of malware based on the publicly available source code, explaining that users should be super-careful when downloading APKs from third-party stores.
 14 DAY TRIAL //
14 DAY TRIAL //