A new Android trojan that's being detected as Android/Spy.Agent.SI is targeting users for the purpose of stealing their banking and Google account credentials.
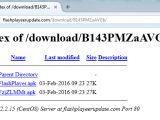
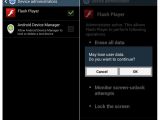
Security researchers from ESET say that the trojan is distributed via websites that advertise a Flash Player for Android devices. Adobe officially stopped developing a Flash client for Android in 2012, so this is an obvious trick to fool users into installing a dangerous APK on their system.
Once downloaded and the installation process started, the trojan will ask for admin rights. Giving it admin rights not only makes it much harder to remove later on but it also grants the trojan the access needed to carry out its attacks undisturbed.
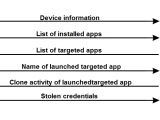
After the installation process is finished, the trojan will behave like most banking trojans today do. It will first collect a list of information about the user's device and then send this to a C&C server.
While in earlier versions this was done via a base64 encoding, later on, the trojan started using better obfuscation and encryption.
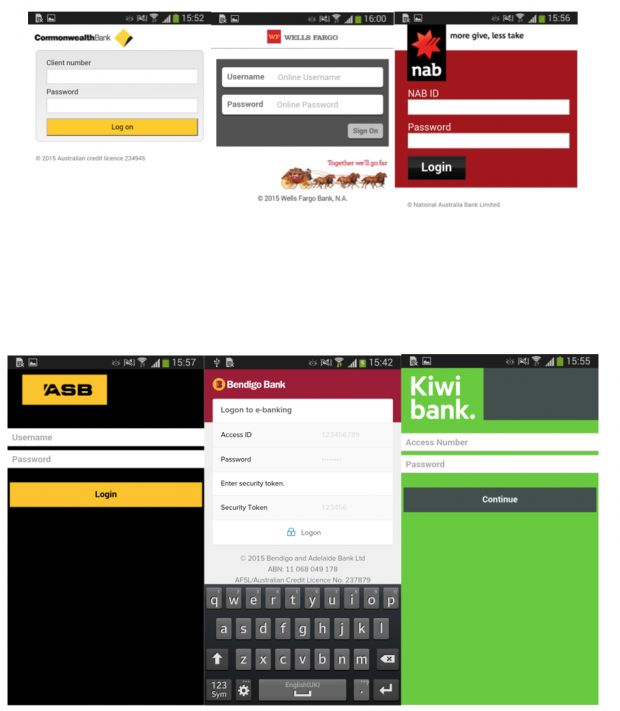
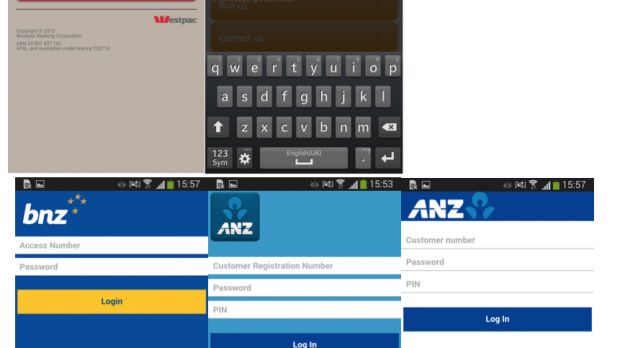
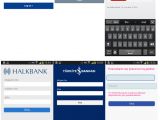
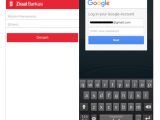
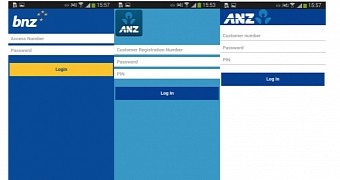
The trojan can mimic the login pages of 20 banks
Once a connection is established between the infected device and the C&C, the server will send it a list of apps it must inject with fake login pages.
These are overlaid on top of the original app whenever the user starts it, and they collect the login info, sending it to the C&C server. Because the trojan fails to encrypt stolen credentials, there's an added danger to infected users because these banking and Google credentials are sent over in plaintext.
ESET says that until now the trojan has targeted financial apps for banks in Australia, New Zealand, and Turkey. Android/Spy.Agent.SI also boasts the ability to intercept SMS messages, in case the spoofed application comes with 2FA (two-factor authentication protection).
ESET provides instructions on how to uninstall the trojan, along with the full list of banks the trojan targets and the websites from where the fake Adobe Flash for Android packages have been found available for download.
 14 DAY TRIAL //
14 DAY TRIAL //