Untrained and gullible Android users are now the target of an Android banking trojan that asks them to send a selfie holding their ID card.
The trojan's name is Acecard and is considered one of the most dangerous and intrusive Android banking trojans known today, according to a Kaspersky analysis from last February.
To stay ahead of security researchers, all malware must constantly evolve, either with changes to their underlying code or in their mode of operation.
New version of Acecard trojan found targeting Singapore and Hong Kong
A previous version of the Acecard trojan hid inside a Black Jack game delivered via the official Google Play Store. In the most recent version of this threat, security experts from McAfee have found a new version of the Acecard trojan hidden inside all sorts of apps that pose as Adobe Flash Player, pornographic apps, or video codecs.
All of these apps are distributed outside of the Play store and constantly pester users with permission requirement screens until they get what they want, which is administrator rights.
Once this step is achieved, the trojan lays in hiding until the user opens a specific app. McAfee experts found that when the user opens the Google Play app, the trojan springs a new social engineering trap.
Acecard tricks the user into providing payment card and real ID details
First, it prompts the user for his payment card number. Then, in separate popups, it asks the user for their card details, such as name and expiration date, but also asks the user to enter their real ID details. At the time of writing, versions of this trojan have been seen asking for ID details specific to users living in Singapore and Hong Kong.
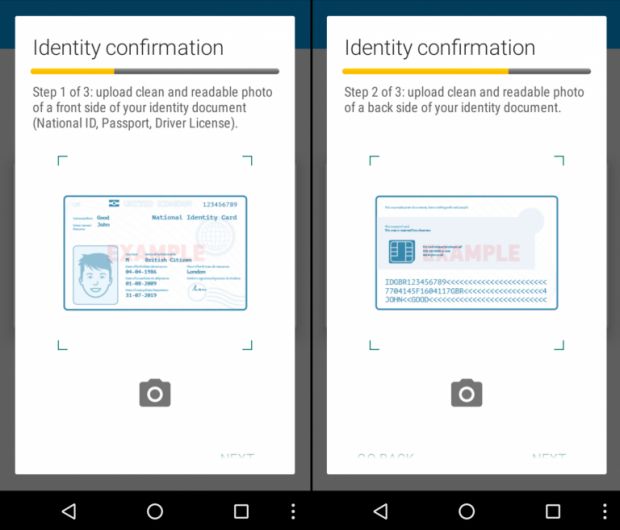
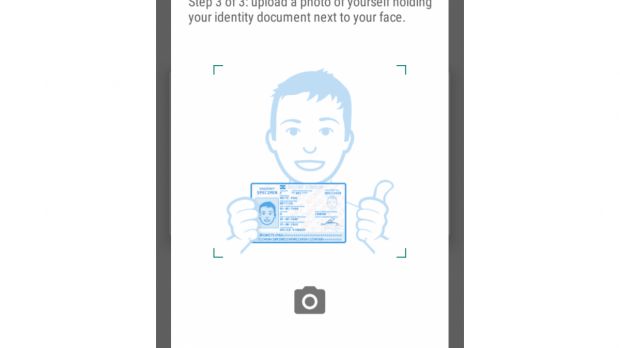
After this, the trojan uses new prompts to ask the user to take a picture of the front and back side of their ID card. During a third step, the trojan then asks the user to hold the ID in their hand, underneath the face, and take a selfie.
ID photo can be used to confirm illegal transfers, take over accounts
"[This is] very useful for a cybercriminal to confirm a victim’s identity and access not only to banking accounts, but probably also even social networks," says Carlos Castillo, McAfee researchers, of the reasons why Acecard is using this new kink.
With photos of the victim's ID in hand, the attacker can verify illegal banking transactions, or confirm to tech support that he's the real owner of hijacked social media accounts.
Besides Google Play, this version of Acecard also collects access credentials using fake logins for social media apps such as Facebook, WhatsApp, WeChat, Line, and Viber, but also other apps such as Dropbox, Google Music, Google Books, and Google Videos.
This trick obviously works only with less technical users, who haven't used smartphones for long. Any tech-savvy users would quickly understand that there's no reason for Google to ask for your ID card, and take measures to find the trojan and remove it from their phone.

 14 DAY TRIAL //
14 DAY TRIAL //