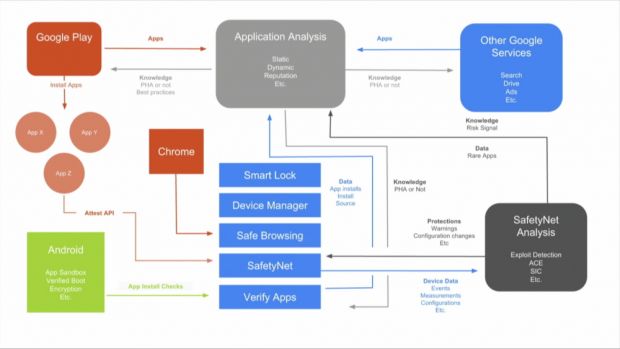
Google debuted Android N last month at the Google I/O conference, but there were so many new things announced at the event that some of Android's security enhancements fell through the cracks. Almost a month later, let's take a look at what Google introduced in terms of new security features for Android N.
First and foremost, Verified Boot is now strictly enforced. While on Android Marshmallow your phone only warned you when something tampered with the boot code, on Android N your phone will refuse to start, and that's that.
Lots of changes for Android's encryption
Hardware-backed keystores will be mandatory as well. Google previously allowed developers the option to store encryption keys in TrustZone, a secure area of the Android kernel. Starting with Android N, the TrustZone will be the only area where you can store encryption keys.
To prevent developers from using weak encryption that can be easily brute-forced, Android devs deprecated the Crypto provider as well.
It's already been mentioned in many articles by now, so you probably know that, in Android N, Google will give users the ability to encrypt data by files.
Previously, Google provided the option to encrypt your entire disk, but users reported performance issues, so to prevent user phones from working overtime to encrypt, decrypt and verify junk files, Google is now giving users the option to encrypt only what they actually need to be kept safe.
Disk-based encryption may be safer than file-level encryption
An interesting point relating to file-level encryption has been raised by Liviu Arsene, senior e-threat researcher Bitdefender, in an interview for TechTarget.
"The downside is that some areas of the file system (i.e. the swap partition) could include unencrypted copies of the encrypted files and an attacker could easily read these," Arsene said. In this case, you might be safer if you use disk-based encryption instead and take the performance dip.
Also on the topic of encryption, Google made updates to the Network API in order to simplify how developers manage and work with HTTPS.
Last year, in Android Marshmallow, Google allowed developers to block third-party SDKs automatically if they didn't use encryption. This year, Google is adding a filtering system that will allow developers to specify on which URLs it is OK to use plaintext HTTP requests, and for what domains HTTPS must be present or the connection won't be established.
Furthermore, the Network APIs has now unified the CA store on all devices, and all user-installed certificates won't be considered as "trusted" by default.
Android gets 11-year-old Linux sandboxing feature
Google has also announced that Android N will feature a "hardened" Mediaserver component. By "hardened," Google was referring to the fact that it split the Mediaserver into smaller sandboxed components.
Since we've brought up sandboxing, for Android N, Google has ported the "seccomp" sandboxing feature from the Linux kernel, not included in the initial Linux kernel fork that gave birth to the Android OS.
Android N will also get the ability to install OS updates in the background and then apply them when the user reboots their device the next time. Additionally, a new indicator called "Android security patch level" will show the date of the last security patch, so you'll know if your mobile carrier has been slacking at delivering security updates.
On top of this, Google has improved the fingerprint authentication mechanism, expanded the permissions model with more granular controls for developers, and introduced a function to allow developers to check a device's health, and see if somebody tampered with the core OS code.
Android N takes the fight to ransomware, banking trojans
To combat malware, Google will be restricting access to the Device Admin APIs. Apps won't be able to change an existing password programatically, and all device admin apps can be uninstalled, which should make removing malware with admin privileges much simpler.
While limiting the ability to change user passwords will make the life of mobile ransomware coders much harder, Android N is going to make it more difficult for banking trojans as well.
Google plans to do this via a change to the SYSTEM_ALERT_WINDOW function, which will now restrict even more the ability of other apps to draw overlays over other apps or system dialogs.
Here is a video of Adrian Ludwig's Google I/O presentation, detailing some of the Android N security features we listed above.

 14 DAY TRIAL //
14 DAY TRIAL //