Malware coders have adapted two Android trojans to cope with Marshmallow's new user permission model, showing that, despite Google's best efforts, crooks will plow through all the company's security measures and still reach their targets, even if in smaller numbers.
Google launched Marshmallow last year. One of the key security features introduced with the mobile operating system was the new permission model that allowed apps to require the necessary permissions at runtime when a certain app function needed access to more data.
Initially, malware coders didn't like this because it spread out all their malicious app's intrusive permissions across different popups, giving users the opportunity to spot something was wrong.
Crooks initially ignored the new permissions model
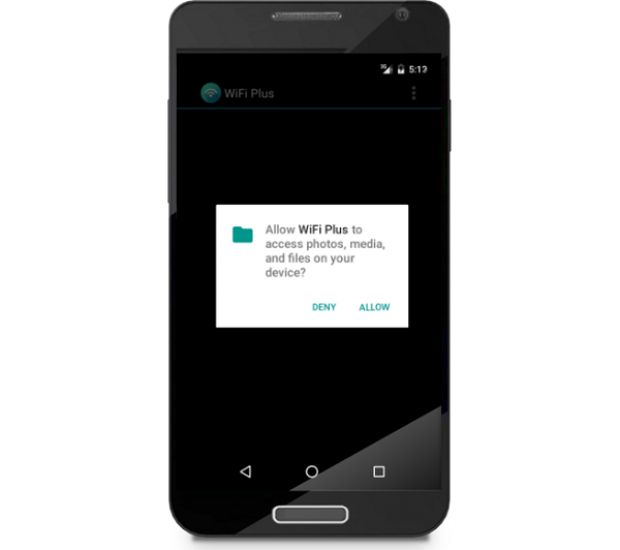
But crooks are resilient, so they adapted by adding the "target_sdk" attribute to the malicious app's code and giving it a value of less than 23. This value told Marshmallow to ask for all permissions at installation, like on older Android OS versions.
While this was fine and dandy in the beginning, security vendors quickly noted this change and took a closer look at Marshmallow apps that employed this trick, and by doing so, brought the malicious applications more into the limelight.
Now, Symantec reports that two malware families, the dangerous Android.Bankosy banking trojan and the Android.Cepsohord click-fraud bot, have evolved to use the new permission model, which they despised in the beginning. Both ask users for permissions at runtime, as they need them.
Furthermore, both trojan also checks at runtime if the permissions are still active. If the user has decided to revoke one or more permissions, the trojan asks for them again.
It's all the same for malware coders
A possible explanation for why malware coders decided to take this road resides in the profile of infected victims. Most people who suffer from such virus infections aren't technically trained experts, educated and experienced enough to spot such threats.
The vast majority are regular users, who often just click through all permissions without reading them. We're all guilty of that, but some people just don't care about permissions anymore, and that's the reason Google decided to split them across different screens.
Malware coders are leveraging on popup fatigue to help their malicious apps get all the permissions they need. In case the user reads permission popups, they would have detected the suspicious malware regardless. In case the user just ignores the popups, they get infected anyway. So it's practically the same for malware coders, who at the end of the day will be successful at infecting the same technically unskilled and uneducated users as before, regardless of whether they ask for permissions in one way or another.
Sure, Android Marshmallow's new user permission system is great and may help users spot abusive and privacy-intrusive apps, but it only works if you know what all those popups and permissions do, and some people don't, and that's why Android malware is so successful right now.
It will take some time before the vast majority of users get truly acquainted with Android and how mobile malware works, but even today, after decades of having Windows around, users still get infected with malware.

 14 DAY TRIAL //
14 DAY TRIAL //