Godless, detected by Trend Micro as ANDROIDOS_GODLESS.HRX, is a malware family affecting Android smartphones and tablets that leverages rooting exploits to escalate its access to device administrator.
Trend Micro says the app is distributed via different methods and from multiple locations, even including Google's Play store, usually considered a safe option for app downloads.
Godless is packed inside various apps, and when allowed to execute, it will download the android-rooting-tools project from GitHub, which is a collection of open-source or leaked exploits to root Android devices.
Godless can root nine in ten Android devices
Based on the source code it analyzed, Trend Micro says that Godless can root all Android versions, starting with Android Lollipop (5.1) and earlier. Based on the portfolio of rooting exploits it possesses, Godless could theoretically root 90 percent of all Android devices in circulation today.
The most potent rooting exploits found in Godless' collection of hacking tools include CVE-2015-3636 (PingPongRoot exploit) and CVE-2014-3153 (Towelroot exploit).
When the Godless infected app runs and after it finishes downloading the rooting exploits, the malware will make sure the user's screen is turned off, and then execute the malicious code.
Godless will download unwanted apps on your Android device
After Goodless gains root privileges, it starts communicating with a C&C server, from where it gets a list of apps to install on the rooted device.
In previous versions of the malware observed a few months earlier, Trend Micro researchers say Godless used to download a clone of the Google Play Store official app, which it would use to collect the user's Google credentials.
With these credentials in hand, Godless would then download and install other apps using the legitimate Google Play Store app.
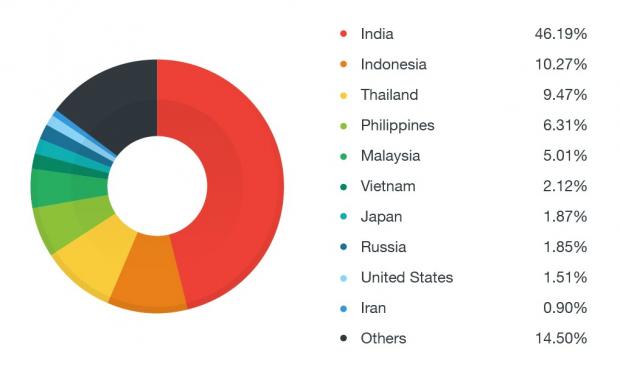
The security firm estimates that Godless has made at least 850,000 victims worldwide. Based on the graphic below, most users are located in India (46.19 percent), followed by Indonesia (10.27 percent), and Thailand (9.47 percent).
At the start of May, Bitdefender discovered a similar Android malware that also employed rooting exploits.
 14 DAY TRIAL //
14 DAY TRIAL //