A mobile banking trojan has just evolved, and while security researchers are quite impressed with the malware author's ingenuity, we, users, aren't that happy to find out that voice-based two-factor authentication (2FA) is not as safe as it once used to be.
Two-factor authentication is an extra layer of protection added on top of classic username-password combos. 2FA relies on a "second factor," which in most cases is a second one-time password sent to users via SMS messages.
Most companies like Google, Facebook, Microsoft, or Twitter have such a system in place, along with online banking portals and other critical-service businesses.
Android malware was already capable of stealing 2FA SMS codes
In recent years, mobile malware has been developed to crack the security of 2FA systems by intercepting SMS messages and also sending their content to fraudsters.
For this reason, 2FA was upgraded to send users the one-time password via voice calls as well, when technically possible. In this scenario, an automated robot calls your phone and speaks out loud the one-time password's numbers and letters.
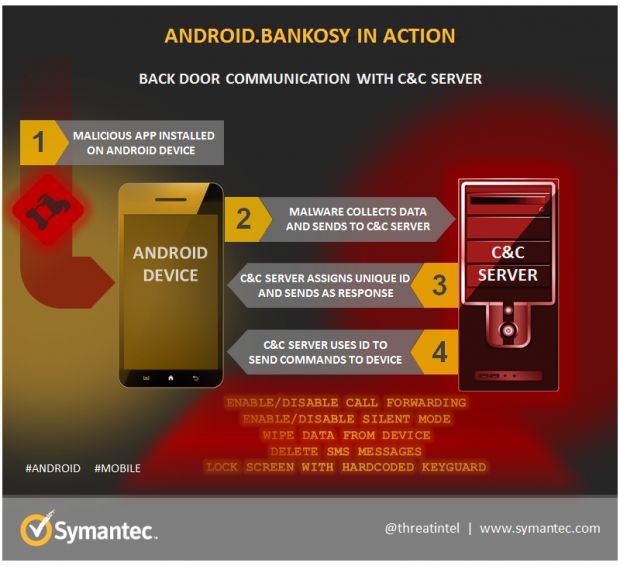
According to Symantec's researchers, an older Android mobile banking trojan has received an update that allows it to intercept these calls and listen on the one-time 2FA code.
Android.Bankosy only targets the users in the Asia Pacific region
Known under the name of Android.Bankosy, this malware was nothing out of the ordinary before receiving this update. The malware infected users via third-party apps, collected data about the victim, sent it to a C&C server, and then logged credentials for financial apps. If needed, Android.Bankosy was capable of intercepting SMS messages to steal 2FA codes.
As Symantec explains, the recent update it has received also allows it to intercept 2FA voice codes by temporarily forwarding voice calls to the attacker's phone number.
This feature has been added only for some Asian countries, where the attacker can easily set up call forwarding on the phone by entering and calling the "*21*[DESTINATION NUMBER]#" access code.
After the attacker acquires the 2FA code sent via the voice call and rerouted to their phone, they can instruct (via the C&C server) the target's smartphone to disable call forwarding by calling "#21#".
Since Android.Bankosy can also lock the phone and put it on silent while sneakily forwarding your calls, this attack can go unnoticed if the user is not interacting with the phone at that particular moment.
 14 DAY TRIAL //
14 DAY TRIAL //