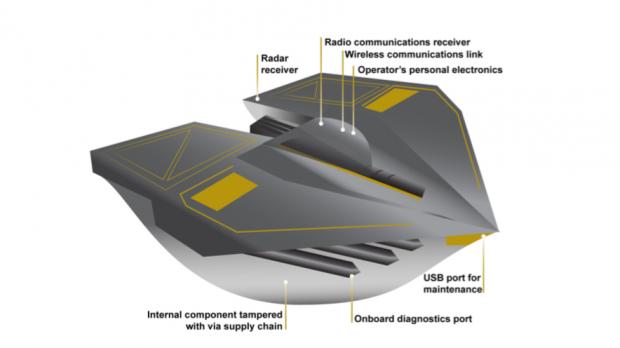
The US Government Accountability Office (GOA) published a cybersecurity report detailing the fact that major weapon systems under development in the current portfolio of the Department of Defense (DOD) suffer from mission-critical vulnerabilities.
As detailed in GOA's report, DOD's latest highly computerized weapon systems provide attackers with a lot more vector attacks than conventional weapon systems.
Moreover, the fact that DOD did not make a priority out of securing its weapon systems from cyber threats has exposed almost all of them to mission-critical security vulnerabilities which would allow threat actors to take control and operating while remaining undetected.
DOD cybersecurity test teams performed routine security tests between 2012 and 2017 concluding that there is no known number or scale of vulnerabilities affecting its weapon systems.
"For example, one assessment found that the weapon system satisfactorily prevented unauthorized access by remote users, but not insiders and near-siders," says GOA's report. "Once they gained initial access, test teams were often able to move throughout a system, escalating their privileges until they had taken full or partial control of a system. In one case, the test team took control of the operators’ terminals."
Also, other testers stated that they were capable of copying, changing, or deleting large amounts of system data from a compromised weapon system, with 100 GB of data being downloaded at one time.
Among the security issues affecting DOD's new weapon systems, unencrypted communications and poor password management were the top ones
Furthermore, GOA testers also reported that nearly all DOD weapon systems could be hacked into with the help of very simple tools and methods which make it easy to take control of the systems,
This happened because of multiple factors among which unencrypted communications and poor passwords management (in one case the admin password was guessed in nine seconds) take the top spots.
The US GOA also states in its analysis that "in some cases, simply scanning a system caused parts of the system to shut down. One test had to be stopped due to safety concerns after the test team scanned the system. This is a basic technique that most attackers would use and requires little knowledge or expertise."
Also, DOD's weapon systems are also vulnerable to unpatched security issues which were reported by GOA's test teams after previous test sessions, with only one out of twenty vulnerabilities previously reported having been corrected in one case.
GOA ended its analysis of the current cybersecurity state of DOD's weapon systems saying that although the DOD has taken some measures to boost their security, it is now facing workforce challenges, as well as vulnerability lessons and sharing information difficulties.
 14 DAY TRIAL //
14 DAY TRIAL //