Mobile security researchers at Lookout have coined the term "trojanized adware" to describe the most recent wave of adware that's been discovered in the Android ecosystem, adware that uses various exploits to install itself as root on infected devices.
As researchers note, this trend is new, and the first signs came when Cheetah Mobile discovered GhostPush (Shedun) in mid-September, and later from FireEye with the discovery of Kemoge (ShiftyBug).
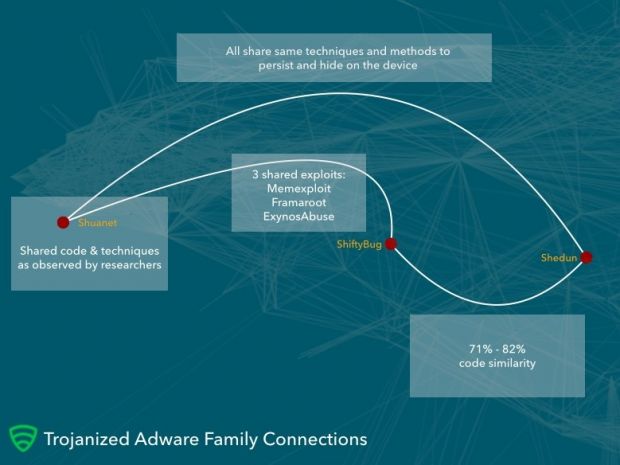
Lookout researchers have identified a third variant of this dangerous type of adware, which they've named Shuanet.
Shuanet shares code with GhostPush and Kemoge
After further analysis of the three families, researchers have been able to find that Shuanet has 71% and 82% similarities with the code of GhostPush and Kemoge.
Besides shared coding techniques, the three also use three common exploits to root the Android device. These are Memexploit, Framaroot, and ExynosAbuse.
Despite the large quantity of shared code, Lookout doesn't believe the three adware families are created and ran by one single group. We propose the theory that they might be bought from the same exploit/malware vendor.
Shuanet spreads through unofficial third-party app stores
As for its modus operandi, Shuanet works just like its predecessors, meaning its authors downloaded popular applications from the Google Play Store, and repackaged them with Shuanet, after which they uploaded the repackaged apps on another Android app stores, which obviously don't employ any security scanning techniques.
Lookout claims that the operation in which the apps were repackaged with Shuanet seems to have taken place automatically (via a script). This theory from Lookout is based on the fact that the adware's operators avoided antivirus and security apps, but when they repackaged apps that handled sensitive information (Okta’s two-factor authorization app), they did not tamper with the process that handles sensitive user information.
Once users are careless enough to download any of the repackaged apps, using the exploits at its disposal, Shuanet roots the device to gain persistence. At this point, Shuanet's operators can start pushing malware, ads, or unsolicited apps.
Lookout researchers claim they have identified over 20,000 official Android apps being offered for download on third-party Android stores, repackaged with either Shuanet, GhostPush or Kemoge.
Most infected users reside in the United States, Germany, Iran, Russia, India, Jamaica, Sudan, Brazil, Mexico and Indonesia.

 14 DAY TRIAL //
14 DAY TRIAL //