After earlier this month Malwarebytes detected an adware installer using a zero-day bug in OS X, the cyber-security firm is now also reporting that the same adware installer is now illegally accessing the Mac Keychain by a very clever trick.
The adware installer, created and distributed by Israeli company Genieo, was caught by one of Malwarebyte's researchers using a loophole in new error logging features introduced in Mac OS X 10.10.4 to allow itself to put adware or malware on the user's workstation without needing a root password.
While this zero-day exploit was not present in the newer El Capitan, Apple fixed it quite quickly to avoid any further problems, especially after it was publicly disclosed.
Now, Genieo has come up with another trick that allows them to install their adware on users' Macs, and this one uses features present in the operating system to assist users with disabilities.
The adware installer will take over your mouse
While many apps may be clean themselves, due to various commercial reasons, they partner with other companies in pay-per-install or bundled installs contracts. Genieo seems to be a company that abuses the trust of its partners.
According to Malwarebytes security researcher Adam Thomas, when installing DealTop, OptimumSearch or MacKeeper, after the user goes through the license agreements, the installer will end by redirecting users to the App Store to download the Download Shuttle app.
After this happens, a small window appears and disappears in a quick flash. During this time the mouse changes position, putting itself over the OK button and clicking it without the user taking any kind of action.
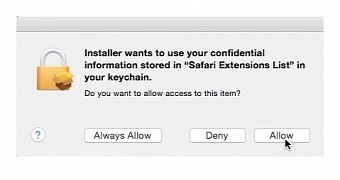
Malwarebytes has analyzed this behavior, and apparently, a hidden adware installer gives itself access to the Safari Extensions List in the Mac Keychain, through which it then proceeds to install the Genieo Safari extension.
Since the Mac Keychain is where various sensitive passwords and access keys are stored, security researchers warn that hackers could use the very same trick to give themselves access to the Keychain and steal all the user's sensitive passwords.
This type of attack was first detected in 2011
The attack basically relies on a piece of AppleScript code. For it to work, the user must first allow the app that runs it access to his Mac.
As Ars Technica is reporting, this trick was being used by Bitcoin miners going back to 2011, and Thomas Reed from Malwarebytes also confirms it also works on Apple's current OS X.
A video demonstration of the mouse-click simulation exploit can be viewed below.
 14 DAY TRIAL //
14 DAY TRIAL // 