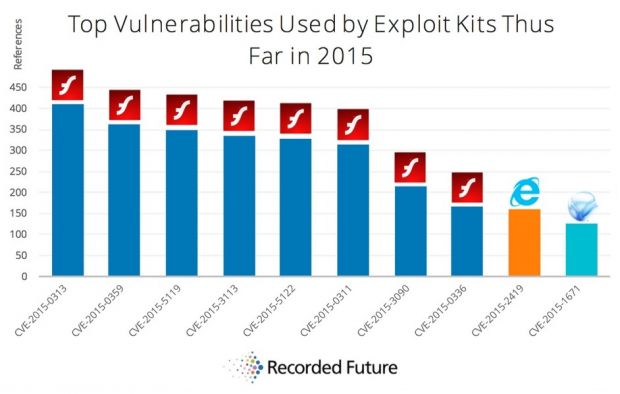
Threat intelligence research company Recorded Future has put together a list of the most used vulnerabilities currently integrated in exploit kits (EK).
Their research covered the period from January 1, 2015, to September 30, 2015, and included data from the analysis of over 100 exploits kits currently used for various types of attack scenarios.
For the uninitiated, an exploit kit is a collection of hacking tools that facilitate the infection of a user's computer with a particular piece of malware, specifically targeting known security vulnerabilities.
Some of today's most famous exploit kits include the Angler EK, the Fiesta EK, the Hanjuan EK, the Nuclear EK, and the Neutrino EK.
By looking at the type of security vulnerabilities exploit kits leverage to deliver their malicious payloads, the researchers from Recorded Future were able to create a top 10 of the most used security flaws.
Nobody was surprised to see Flash in the Top 10
As everyone expected, the top spot went to a Flash vulnerability, of which Adobe had plenty this year. In fact, Flash was so plagued by security issues that the first eight spots in the top 10 went to various security flaws discovered this year alone.
Coming in on number 9, we find an Internet Explorer bug, followed by another Microsoft product, the deprecated Silverlight platform.
All the top 10 vulnerabilities are issues discovered this year, showing that EK operators don't generally waste time when it comes to integrating the most recent security bugs into their code.
While many have mitigated for deprecating and giving up on Flash, including Facebook's CSO, the reality is that Flash Player still accounts for a huge market share.
What makes it even worse is another recent study carried out by Secunia (now part of Flexera Software) which points to the fact that 80% of all Flash users don't run the most recent version of Flash.
This means that despite Adobe's best efforts in keeping Flash Player bug-free, users still run outdated versions, even using versions marked as EOL (End-of-Life).

 14 DAY TRIAL //
14 DAY TRIAL //