Security experts at BinaryEdge have analyzed how developers and system administrators configured different technologies and have found out that most of them fail to change the default configuration, which leaves their servers open to outside intrusions.
The same kind of research was also carried out in the past by a group of students who found 40,000 MongoDB databases exposed to Internet connections, and by John Matherly, founder of Shodan.io, who found 600 terabytes of data exposed in 30,000 MongoDB instances, only four months later.
The BinaryEdge team went over the same procedures, scanning the Internet on various ports, seeing which servers answered.
Almost 1.2 petabytes of information is exposed online
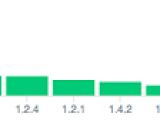
Only four technologies were included in their study, which revealed 1,175 terabytes of information. The technologies in question are Redis, MongoDB, Memcached, and ElasticSearch, all suffering from the same issue - using the default configuration which does not block connections from untrusted external actors.
The first one they scanned for was Redis, a NoSQL key-value store widely used around the Web development community.
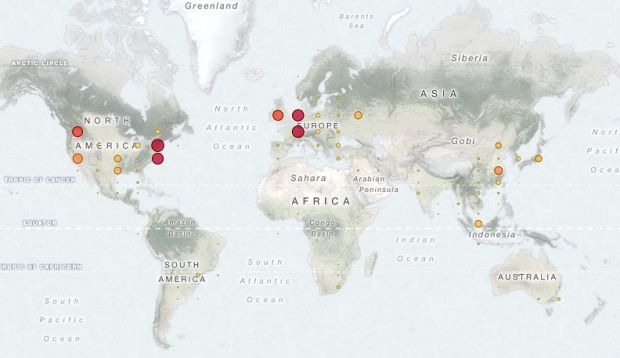
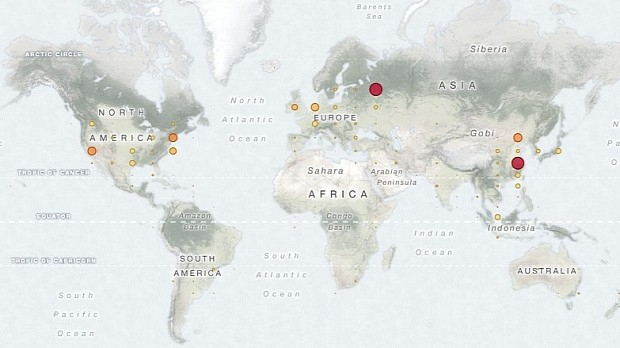
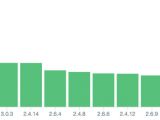
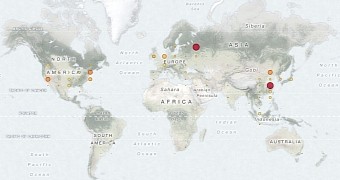
Their findings revealed 35,330 Redis instances that accepted external requests, exposing around 17 terabytes of data, mostly in data centers in China and Russia.
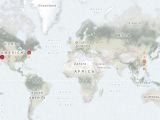
The same thing goes for MongoDB, as the researchers found 39,134 MongoDB servers online, mostly in the US and China, exposing 619 terabytes of data.
The funny thing about these two NoSQL database engines is that they both have a special section on their websites where database administrators are warned not to use the default config file in production environments.
Caching solutions and search servers are also left open
BinaryEdge researchers then moved on to Memcached, a distributed memory caching system, which just like Redis and MongoDB comes with a default config that allows for external connections.
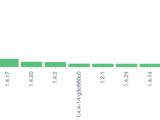
According to the researchers, over 118,574 Memcached instances were found online, mostly in the US, exposing 11 terabytes of data.
The last technology they scanned for was ElasticSearch, a search server technology widely used in multiple domains.
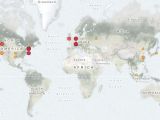
The BinaryEdge team found only 8990 instances exposed in this case, mostly in Western Europe and the US, but they were exposing a whopping 531,199 terabytes of information.
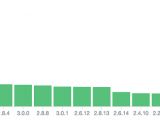
As the researchers conclude, besides the exposed data, they've also found that most of the exposed server instances are running older versions of the technology in question, which in some cases, besides leaving the data out in the open, also expose the entire server to more serious security issues.
Additionally, the data they've found did not reside in test servers alone, some of the exposed servers belonging to Fortune 500 companies.
 14 DAY TRIAL //
14 DAY TRIAL //