The OpenSSL project has released versions 1.0.2g and 1.0.1s to address a high severity security issue known as the DROWN attack (CVE-2016-0800) which allows attackers to break HTTPS and steal encrypted information.
DROWN stands for "Decrypting RSA using Obsolete and Weakened eNcryption" and it was discovered by a team of 15 researchers from various universities and the infosec community.
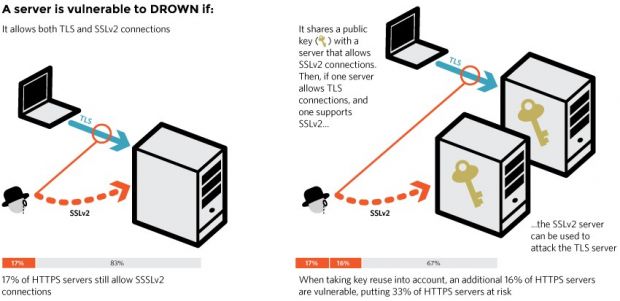
At its core, the principle behind the DROWN attack relies on the presence of both the SSLv2 and TLS protocols on target machines. DROWN is a cross-protocol attack, meaning it will use weaknesses in the SSLv2 implementation against TLS.
DROWN is the second coming of the Bleichenbacher attack
The weakness comes from the Bleichenbacher attack on RSA, an encryption system used by both SSL and TLS. Before establishing an encrypted connection, a client will choose a random session key which is encrypted via RSA (and the server's publicly-advertised key) and sent to the server which then validates the client and starts an HTTPS connection.
The Bleichenbacher attack, discovered in the late ‘90s found a way to obtain the original RSA key just based on a server answering "yes" or "no" to the question "is this the RSA session key?"
Researchers behind the DROWN attack found new ways of launching the Bleichenbacher, taking advantage of the fixes added to SSLv2 to protect against it.
DROWN affects TLS due to improperly configured servers
The attack works on TLS, a protocol considered to be superior to SSL, because regardless of the differences between them, both protocols use the same RSA-encrypted session key to generate the actual HTTPS connection.
The only servers vulnerable to this issue are those that are still using both SSLv2 and TLS at the same time, so disabling SSLv2 on your server should be the first thing on your to-do list. Additionally, the researchers are also warning against a particular server setup that could expose sysadmins to DROWN, even if the main website only uses TLS.
"You’re just as much at risk if your site’s certificate or key is used anywhere else on a server that does support SSLv2," researchers noted. "Common examples include SMTP, IMAP, and POP mail servers, and secondary HTTPS servers used for specific web applications."
Widespread RSA key reuse makes this attack even more dangerous by exposing servers where administrators took the necessary steps to remove the insecure SSLv2 protocol, but forgot to secure TLS with new RSA keys.
One DROWN attack per website costs $440
During their tests, researchers said that around 33% of all HTTPS websites are vulnerable to this attack. Some of the most reputable sites vulnerable to DROWN include Yahoo, Weibo, Alibaba, xHamster, DailyMotion, BuzzFeed, Flickr, StumbleUpon, 4Shared, HostGator, and many other more.
Researchers say they don't believe DROWN has been used in live attacks. They say that running the attack involves "a moderately large computation," but that a full attack on a domain only requires 40,000 probe connections ("is this the RSA session key?" questions), 250 computations, which adds up to around a $440 / €405 bill on Amazon EC2.
More technical details, a list of the top vulnerable websites, and a DROWN Vulnerability Checker can be found on the DROWN Attack website. You know a security flaw is important when it has its own website.
Additionally, Matthew Green, a famous cryptographer and professor at Johns Hopkins University, has also penned a blog post explaining how DROWN works.

 14 DAY TRIAL //
14 DAY TRIAL //