Computer users in the United Kingdom are assaulted by phishing emails claiming penalties for unpaid parking and containing a variant of the Zeus Trojan disguised as a PDF file.
Zeus Trojan, also known under the name of Zbot, is famous for its infostealing capabilities that target sensitive banking details and online credentials.
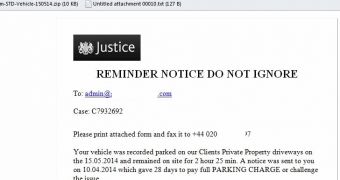
The email, with the subject line “Reminder notice do not ignore,” has the letterhead of the UK Ministry of Justice and informs the potential victim that they have to pay £72/$122/€90 as a result of penalties accumulated in 28 days.
It also says that a previous notice has been sent, allowing the victim to challenge the issue of paying the fine.
There are vague details about the driveway where the car was parked, but the scammers are accurate as far as the parking duration is concerned. An attachment is provided for “photographic evidence.”
To make the matter look legitimate and convince the user to download the attachment, the perpetrators elevate the alleged risks of not paying the fine by saying that one of the consequences could be the inability to obtain credit in the future.
“Failure to pay the full outstanding balance within 14 days of the date of this notice could result in the outstanding balance being registered as a debt against you,” the message reads.
The file (Form-STD-Vehicle-150514.scr) is a malware dropper, identified by Bitdefender as Trojan.GenericKD.1681628, and it proceeds to download the Zeus Trojan variant.
Bitdefender researchers determined that the dropper connects to a pharmaceutical website that is under the control of the criminals. It is unknown whether it is a legitimate location compromised by the attackers or a website specifically created for nefarious purposes such as malware distribution.
The Zeus variant is then executed and the system infection is complete.
Apart from stealing sensitive information that can lead to financial fraud, the threat can also receive remote instructions to download other types of malware or components that would increase its stealing capabilities or improve antivirus evading tactics.
It appears that such emails began invading the inboxes of UK citizens a couple of months ago, with a spike recorded on May 15. According to Bitdefender, “in a two-hour period, one out of five samples was a bogus parking fine message.”
Attachments coming from suspicious sources should never be opened. Some of the signs of deceit include the email address from which the message was sent, which in this case is justice.gov.uk instead of the real one, that is [email protected].
 14 DAY TRIAL //
14 DAY TRIAL //