Unlike most crypto-malware ransomware announcing the encryption of the files on the computer and asking for a fee to unlock them, the new ZeroLocker claims to be a decryption tool that can rescue the data locked by a different threat, if a license of the program is purchased.
This is just a small variation of the ransomware model adopted by the cybercriminals, but the endgame is always the same: the victim has to pay a fee for getting the data decrypted.
Security researchers from Webroot analyzed the piece of malware and determined that it is far less complex than crypto-malware such as CryptoLocker as the threat presents a flaw that allows rescuing the data without having to pay the ransom.
Tyler Moffitt says that ZeroLocker does not delete the Volume Shadow Service (VSS), which is responsible for creating backups (automatic or manual) of files on the computer even when they are in use.
If activated, it can make safe copies when Windows Backup component is started or when creating an automatic system restore point for any volume on the system.
Unfortunately, most users have System Restore enabled only for the system drive and the default backup solution is not always used.
This flaw in the malware could be eliminated in the next versions, security researchers warn, leaving users that do not have backup copies for their files no chance but to pay the ransom or to lose the data.
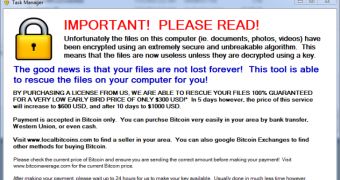
In the ransom message, the malware author affirms that the data has been locked “using an extremely secure and unbreakable algorithm.”
This would mean that the threat relies on a complex cryptographic scheme that involves key pairing for encrypting and decrypting the information.
In such a case, the files are locked using a public key and the decryption is carried out with a private key that needs to be protected.
With ZeroLocker there is no information on the encryption method employed, but chances are it is not too advanced.
After the computer is infected, ZeroLocker starts encrypting the files immediately and once the process is completed, the system is restarted and the ransom message is displayed.
The fee is demanded in Bitcoins worth $300 / €225 and there is a deadline of five days to transfer the money to a given address. After this period, the fee increases to $600 / €450, reaching $1,000 / €750 in ten days.
One of the best ways to keep the data on the computer safe is to make backup copies and store it either online or offline, on a drive disconnected from the affected system.
 14 DAY TRIAL //
14 DAY TRIAL //