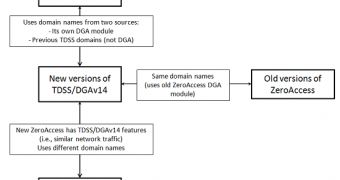
Security researchers from Trend Micro say they’ve found a link between two notorious rootkits: ZeroAccess and TDSS. Experts say they’ve discovered that ZeroAccess uses the randomly generated domains utilized by the DGAv14 variant of TDSS.
Trend Micro made the discovery while analyzing some traffic the company believed was sent by TDSS DGAv14 malware. Experts found that the traffic was actually generated by ZeroAccess/SIREFEF versions. In one single day, the same domain name was used by both ZeroAccess and TDSS.
This is not the only connection found by researchers between the two threats. Both pieces of malware encode traffic by using base64 and they both pad it with garbage characters at the beginning and end. Initially, this method was only utilized by TDSS.
“However, this does not mean that ZeroAccess is now imitating TDSS. We believe that the domain generation algorithm module used by older ZeroAccess malware has now been adapted by TDSS specifically the DGAv14 variants,” Trend Micro Threat Solution Engineer Yuki Chen noted.
While this shows that there might be a connection between the rootkits, there are still some differences.
“Both still maintain separate P2P networks, with similar features but different implementation. In addition, ZeroAccess always infects COM objects and service.exe, whereas TDSS always infects the MBR. ZeroAccess will also disable TDSS on systems that the former infects,” Chen noted.
The fact that TDSS and ZeroAccess share some common features doesn’t necessarily mean the cybercriminals that run them are directly collaborating. Instead, experts believe the two groups might have acquired the domain generation algorithm from a third party. It’s also possible that the cybercrooks behind TDSS are making money by hosting parts of ZeroAccess.
Trend Micro says it will continue to monitor the threats to see if new similarities emerge.
 14 DAY TRIAL //
14 DAY TRIAL //