Activity from the peer-to-peer (P2P) botnet ZeroAccess, also known as Sirefef, was recorded by security researchers on January 15, after a period of idleness that lasted since July 2, 2014.
The botnet came back to its old habit of distributing click-fraud templates to compromised systems, but no increase in its size has been observed, Dell SecureWorks researchers say. This means that it relies on residual hosts infected in the past.
Take-down efforts did not fully shut down the operation
In December 2013, law enforcement agencies in Europe and the United States together with Microsoft and A10 Networks joined efforts in an operation to take down ZeroAccess. Its P2P architecture, however, made it resilient to complete disruption as each infected computer in the network could act as a command and control (C2C) server for the others.
A P2P structure ensures that the botnet can be resurrected at any time by its operators, unless all compromised systems are cleaned.
Click-fraud is not directed at the user because its goal is not to steal sensitive information, but it does generate losses to the advertisers, who are forced to pay for advertisements that are accessed by bots and not by humans, thus defeating the purpose of a campaign.
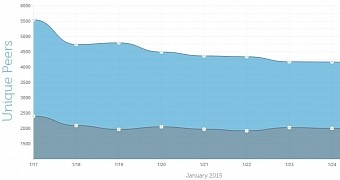
Dell SecureWorks Counter Threat Unit (CTU) research team notes that the threat actors behind ZeroAccess have not tried an expansion of the network, thus resulting in a smaller botnet.
Japan is first on the list with most infections
However, “smaller” still refers to tens of thousands of computers, as 55,208 unique IP addresses have been seen to take part in the malicious operations, 38,094 of them being 32-bit hosts and 17,114 running on the 64-bit platform.
“ZeroAccess is segmented into two distinct botnets that operate over different UDP ports: UDP 16464/16471 - used by compromised Windows systems running on a 32-bit architecture and UDP 16465/16470 - used by compromised Windows systems running on a 64-bit architecture,” a blog post from CTU informs.
According to telemetry data from Dell, the most affected country is Japan, accounting for 27.7% of the infections, followed by India (13.5%) and Russia (12.9%). Other countries where compromises have been detected are Italy (6.6%), the United States (4.6%), Brazil (3.9%), Taiwan (3.8%), Romania (3.5%), Venezuela (2.2%) and Germany (2.0%).
 14 DAY TRIAL //
14 DAY TRIAL //