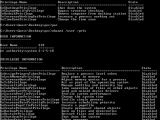
Various security vendors warned today about the public availability of exploit code for a previously unknown Windows privilege escalation vulnerability that can be used to bypass UAC.
The vulnerability was disclosed on a programming portal called CodeProject, but the page has since been removed by the site's administrators.
The flaw is located in the Windows kernel-mode device driver (win32k.sys) and allows attackers with limited access to execute code as SYSTEM.
According to BitDefender, the vulnerable API is called RtlQueryRegistryValues and can be exploited by creating a malformed registry key.
An important aspect of this vulnerability is that it allows bypassing the User Access Control (UAC), a security feature designed to prevent the execution of unauthorized code in Windows 7 and Vista.
Despite the initial disclosure page being taken down, proof-of-concept exploit code has already made it's way onto exploit-db.com and is currently available to anyone interested in it.
Giving the nature of the vulnerability, antivirus vendors expect to see it exploited in malware attacks very soon. Microsoft has yet to comment on the issue.
One malware that made use of similar elevation of privilege (EoP) flaws in Windows is the infamous Stuxnet industrial espionage worm discovered earlier this year.
In fact, one of the two EoP vulnerabilities leveraged by Stuxnet remains unpatched to this day. Earlier this week we reported that exploit code for it has also been publicly released.
Chester Wisniewski, a senior security advisor at Sophos, notes that one possible mitigation involves setting the user's permissions for the "HKEY_USERS\[ACCOUNT_SID]\EUDC" registry key to Deny Delete and Create Subkey. The SID can be determined by typing "whoami /user" in a command prompt window.
With this new announcement, Microsoft currently has three zero-day vulnerabilities on its hands. In addition to the Stuxnet EoP, a critical Internet Explorer arbitrary code execution flaw is also being exploited in the wild.

 14 DAY TRIAL //
14 DAY TRIAL //