There’s a site out there called gotofail.com which tests a user’s configuration and determines whether their computer is vulnerable to Apple’s “gotofail” blunder, the SSL flaw that has been widely reported in the media for the past few days.
It’s no mystery that Apple isn’t the quickest of cats when it comes to patching holes in its software, be it mobile or desktop-bound.
In fact, in recent years, the Cupertino giant has been more focused on the security of its mobile OS than its Mac OS. The latest such example was the SSL/TSL issue that it patched in its mobile software with iOS 7.0.6 and iOS 6.1.6, but left the same hole open on OS X 10.9 Mavericks. It stayed that way for two days, until the company finally delivered OS X 10.9.2.
Although it was already planning to deploy OS X 10.9.2, Apple took two full days – since the discovery of the desktop flaw – to put the finishing touches on the update, include the SSL patch, and roll it out publicly.
In the interim, someone decided to rig up a site to check your configuration for the flaw. Basically, if you have OS X 10.9.2 installed, you should be fine. If you don’t, it might tell you something like the message below, in case you’ve navigated to gotofail.com using Firefox or Chrome.
“Warning! We have examined your OS and browser version information and have determined that your browser shouldn't be vulnerable, however other applications on your system such as mail, chat, financial, social networking and backup apps are at risk. Please re-run this test from Safari to confirm!”
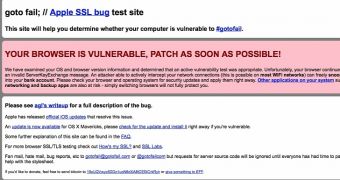
If you do as you’re told and run the site in the vulnerable Safari (again, if you do not have OS X 10.9.2 with Safari 7.0.2 installed), it should tell you that “your browser is vulnerable, patch as soon as possible.”
It then adds, “We have examined your OS and browser version information and determined that an active vulnerability test was appropriate. Unfortunately, your browser continued loading our test image after seeing an invalid ServerKeyExchange message.”
The author of the site explains that, because your system failed to pass the security test, “An attacker able to actively intercept your network connections (this is possible on most WiFi networks) can freely snoop on you, for example when you log into your bank account.”
“Please check your browser and operating system for security updates and apply them right away. Other applications on your system such as mail, chat, financial, social networking and backup apps are also at risk - simply switching browsers will not fully protect you,” the site’s author adds.
Needless to point out, if this is you, we recommend that you download OS X Mavericks 10.9.2 as soon as possible. If you’re running an older version of the Mac OS, Apple offers Security Update 2014-001 to fix the latest security issues.
 14 DAY TRIAL //
14 DAY TRIAL //