A security flaw in the Yik Yak anonymous social media platform for iOS allowed an attacker not only to find the identity of a user but also to take over their account.
The service is designed to offer its clients the possibility to share personal information with a larger group of users in a limited area around the sender, without revealing their true identity. Because of this, the app has grown popular among young individuals in high schools and colleges.
Third-party component makes service vulnerable
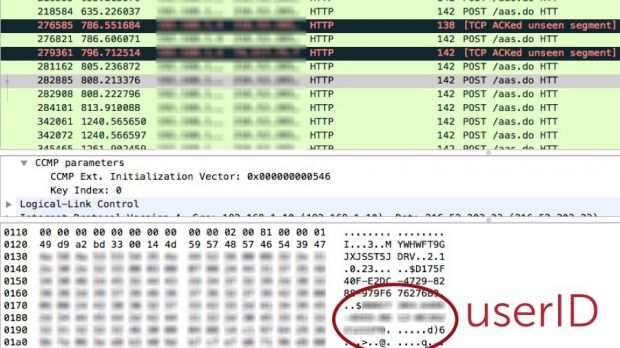
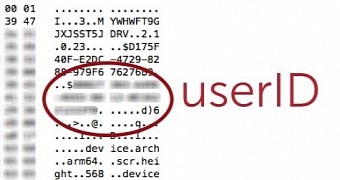
Cloud security solutions provider SilverSky discovered a vulnerability in the platform, which consisted in revealing the user ID to anyone on the same network as the victim.
By Yik Yak’s log-in model, users do not need passwords for their accounts, only an ID that should remain private at all times. Communication to the Yik Yak server is encrypted, but there are other services the client sends traffic to, which do not communicate securely, exchanging sensitive information in plain text.
In the case of Yik Yak, advertising tool Flurry was the weak link, as all the traffic to its servers was delivered in the clear. Since the third-party component collects data to create statistics, and the user ID is the only way to log into the social media account, the sensitive detail is obviously sent to Flurry machines.
Easy way to discover the identity of a victim
The security experts have said that Flurry is called every time the app is started. Needless to say that sniffing the network and pinpointing the call to the third-party service gets the attacker the user ID of a client; since no passwords are required to log into the service, the malicious actor can take control of the account.
As Sanford Moskowitz explains in a blog post, learning the identity of a user can sometimes be just a matter of reading the hostname value of a machine, which may offer additional information about the unsuspecting victim.
“An attacker is able to view all of the target’s previous posts, make new posts, and literally log in to the app using the target’s credentials. This attack can be easily conducted by anyone on the same network as the target; which is a very common situation for Yik Yak’s main demographic: college students,” Moskowitz says.
The researchers informed the developers of Yik Yak of the issue at the beginning of the month and a new update was released the next day.
 14 DAY TRIAL //
14 DAY TRIAL //