WordPress websites with old, vulnerable versions of Slider Revolution (RevSlider) plugin are currently compromised by hackers, who use them to redirect visitors to locations serving malicious code.
Outdated plugins are often the weak spot in WordPress websites, not just because they are more likely to harbor vulnerabilities but also because admins delay applying the patches released by the vendor.
The security flaws in RevSlider that are leveraged by the attackers at the moment were addressed by the developer of the plugin more than a year ago, but many administrators did not apply the patches, leaving their WordPress websites exposed to cyber attacks.
Also accounting for the large number of outdated versions is the fact that RevSlider is often integrated into WordPress themes, whose authors fail to roll out an update for the component as well.
Unwanted traffic is dumped to Bitcoin.org
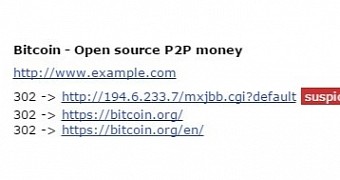
Recently, researchers at website security company Sucuri observed that many hacked websites redirected the traffic from certain web browsers to bitcoin.org, a reputable location dedicated to helping the development of Bitcoin digital currency.
However, the traffic is the result of a verification in a previous location, where it is determined if the visitor’s machine can be compromised via the exploits cybercriminal has at hand. The analysis is based on parameters such as IP address, browser type or referrer.
If the system can be infected, the visitor is redirected to a site that serves a specific exploit. The traffic originating from systems that are not vulnerable is dumped on the Bitcoin website.
According to Sucuri’s Denis Sinegubko, some of the malicious redirects point to a JavaScript code specifically created to attack Internet Explorer.
In the initial stage of infection, the script checks the system for the presence of products that could detect the ensuing malicious activity (antivirus products from Kaspersky or Trend Micro, and virtual machines VMWare, VirtualBox or Parallels). If none are found, it drops an exploit for Flash Player browser plugin.
Most infected sites run an outdated RevSlider
Although websites running different content management systems (CMS) are targeted in the campaign, Sinegubko says that most of them have WordPress installed with old versions of RevSlider.
“We saw many massive attacks that exploited these vulnerabilities over the past six months, and thousands of webmasters learned the importance of timely plugin updates the hard way. Nonetheless, there are still many sites out there that use outdated themes and plugins. Inevitably, hackers find such sites and compromise them,” Sinegubko says.
Administrators are strongly recommended to update their WordPress plugins to the most recent version, especially since a cross-site scripting (XSS) bug has been plugged in a large number of popular components.
WordPress should also be updated to version 4.2.1 because it fixes another XSS flaw that impacts all previous releases.
 14 DAY TRIAL //
14 DAY TRIAL //