At the beginning of April, researchers from Incapsula revealed that a vulnerability in the website of a high-profile video content provider was being abused by cybercriminals to launch large-scale distributed denial-of-service (DDOS) attacks. It turns out that the website is Sohu.com.
Many people rushed to assume that the “high-profile video content provider,” which Incapsula didn’t name before the vulnerability was patched, was YouTube. It turns out that it wasn’t YouTube, but Sohu.com, China’s 8th largest website.
Sohu, which translates as “search fox,” is one of China’s most popular web portals. It provides online media, gaming, search, community and mobile services. While Sohu is not very popular among users in the West, according to Alexa, it’s currently the 27th most visited website in the world.
The cybercriminals found a cross-site scripting (XSS) vulnerability in Sohu.TV, the company’s video streaming service. Fortunately, Sohu employees quickly patched up the security hole after being notified by Incapsula.
“Once we uncovered the source of the browser-based DDoS attack and replicated persistent XSS vulnerability that allowed it to occur we immediately went on to share our findings with Sohu security team,” Incapsula researchers explained.
“With this information in hand Sohu team could quickly evaluate the problem and respond with a rapid patch which fixed the security hole, rendering this browser-based botnet completely useless.”
Incapsula discovered the attack technique after one of their customers suffered a DDOS attack involving 20 million GET requests coming from more than 22,000 web browsers.
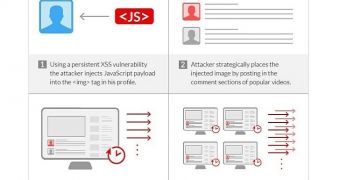
The attackers didn’t compromise the computers of 22,000 users. Instead, they leveraged the persistent XSS flaw to inject JavaScript code into the <img> tag associated with the images on Sohu profiles.
The profiles in question were used to post comments on popular videos. Each time one of these videos was loaded, the malicious code embedded inside the profile image was executed, launching a DDOS attack against the designated target.
The GET requests were sent out at a rate of one per second. This might not seem much, but considering that some videos are up to 30 minutes long, and that a large number of users were viewing the same video at any given time, it was enough to disrupt a website that didn’t use any DDOS protection.
As experts noted in their initial post, the attack against their customer might have been a test run. At the time, they noticed that the command and control (C&C) domain was replaced with one that was more robust. Furthermore, the cybercriminals were also implementing what appeared to be a billing mechanism.
 14 DAY TRIAL //
14 DAY TRIAL //