Administrators of the official White House website rushed to address a cross-site scripting (XSS) vulnerability after being notified by security researcher Ucha Gobejishvili.
According to his personal blog, the Georgian security expert identified the flaw on March 21 and immediately notified White House representatives regarding its presence.
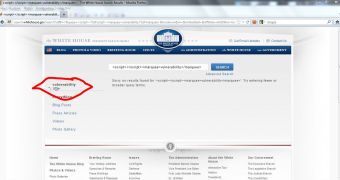
The XSS security hole was present in the search module of the site and it could have allowed a remote attacker to change the site’s appearance by replacing legitimate content with his own malicious one.
As the image provided by the researcher demonstrates, with a certain amount of user interaction a hacker would have been able to place any type of malicious content on the site.
Since social engineering is not a big issue for highly skilled cybercriminals, the vulnerability could have been easily exploited if left unaddressed.
This is not the first time when the site of the White House is found to contain weaknesses that leave it exposed to cybercriminals. In November 2011, Alexander Fuchs and Benjamin Kunz Mejri, experts part of the Vulnerability Research Laboratory, identified a persistent XSS in the petition section of the site.
“The petition system is vulnerable. Every Petition i start or join will execute my code. I could join all petitions and my code will be executed on all users who visit the petition system,” Fuchs said at the time.
Judging by the interval it took the site’s administrators to address the issue back then and also on this occasion, we can safely say that White House representatives take security seriously.
Of course, this is a good thing, especially since the website is a tempting target not only for hackers who want to test their skills, but also for ones that want to cause harm.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile.
 14 DAY TRIAL //
14 DAY TRIAL //