URLs to articles in New York Times (NYT) published before 2013 have been found to be vulnerable to an XSS (cross-site scripting) attack capable of delivering code to be executed in the context of the web browser.
A mathematics student from Singapore by the name of Wang Jing reported on Thursday the XSS flaw affecting the readers of the online newspaper. He also created a video demonstrating the attack on the pages of several old NYT articles.
Vulnerable pages meet certain conditions
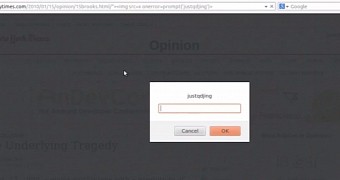
An XSS flaw stems from insufficient user input validation and allows a threat actor to serve malicious code to those clicking on the malformed link. Basically, bad JavaScript is added after a double quote in a legitimate link and is then executed.
The potential risk is evident, since the attacker could hijack browser sessions, steal cookies or direct to phishing websites.
Jing said in the vulnerability report that “all article pages that contain ‘PRINT’ button, ‘SINGLE PAGE’ button, ‘Page *’ button, ‘NEXT PAGE’ button are affected.”
The researcher said that he tested the attack on Firefox (26.0) in Ubuntu (12.04) and IE (9.0.15) in Windows 7 and that no user login is required, as you can also see in the video demonstration below.
A set of live proof-of-concept links have also been provided, but pasting them in the web browser simply loads the article and nothing more.
Even if the articles are old, the pages are still relevant
An attack on more recent articles would definitely have had a significant impact, but articles from 2012 or even older are far from being obsolete. They would still be relevant in the context of an attack.
Cybercriminals can devise various ways to send the link to potential victims and record high success rates, all the more with targeted attacks.
Articles are often provided in reference to something current, and even if this would not be the case, simply sending an email to an interesting article on New York Times could make victims.
Jing said that the reason more recent pages are not exploitable this way is that New York Times added a better protection for the links sent to its server sometime in 2013.
Some web browsers come with built-in protection against this type of attacks. We noticed that the live proof-of-concept do not work at the moment on the latest versions of Internet Explorer, Google Chrome and Mozilla Firefox.
Check out the video with a proof-of-concept XSS attack on New York Times:
 14 DAY TRIAL //
14 DAY TRIAL // 