Two security researchers have discovered a serious XSS weakness affecting the popular micro-blogging platform Twitter. By clicking on a hidden, maliciously crafted link, users can be forced to post messages without their knowledge.
Lance James and Eric Wastl, security researchers for Secure Sciences Corporation, have announced that Twitter users are exposed to potentially dangerous attacks, because of a cross-site scripting vulnerability. XSS flaws are the result of poor input validation and generally allow attackers to force unwanted behavior through simple URL manipulation.
In order to back up their claim, the two white-hat hackers have set up a proof-of-concept URL, which they have shortened and masked with the help of the TinyURL service. Twitter enforces a 140-character limit for messages, thus making the use of URL shortening services like TinyURL almost a must. Cyber-criminals often use XSS weaknesses to inject rogue IFrames into legit and popular pages, but in this case, the two researchers have employed it to abuse the status-update feature. However, the potential for abuse is much greater.
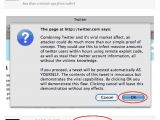
The shortened version of the PoC link has since been disabled by TinyURL, yet the full URL is still available. Clicking on it will first warn users of what they are about to do and ask them if they want to proceed. Hitting "Ok" will automatically post a message that reads "@XSSExploits I just got owned!," on their Twitter page.
"With a technology such as twitter, I could use it to infect massive amounts of twitter readers/users, say with malware or steal their accounts, etc.," Lance James explains for The Register. This is even more dangerous, as most Twitter users have gotten accustomed to simply clicking on TinyURL links without using the service's preview feature to see where they actually lead.
A similar unauthorized-message posting behavior has been previously achieved on Twitter with the help of a technique known as clickjacking. Several proof-of-concept "clickjacking worms" were launched by various individuals on the micro-blogging website, for example, causing users to unwillingly spread a link that ironically read "Don't click!"
So far, these examples have been harmless, but they outline the potential dangers Twitter users are exposed to. Sooner or later, ill-intended individuals will discover such vulnerabilities on their own and will launch serious attacks. So far, the Twitter staff has acted quickly to address them, so hopefully it will do the same in the future.

 14 DAY TRIAL //
14 DAY TRIAL //