A newly discovered Twitter cross-site scripting vulnerability has been used to create an XSS worm that forces users to re-post hidden code by simply rolling the mouse over it.
The vulnerability appears to stem from the way Twitter parses links that contain the @ character, which has special meaning on the micro-blogging platform, as it is used to mark accounts.
Apparently, the flaw causes everything after the @ character to be returned back to the browser as real code.
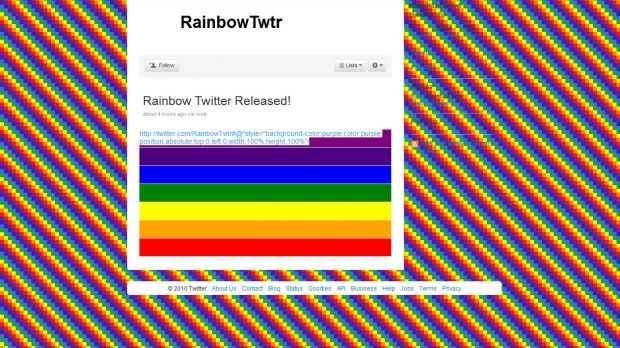
At first, people began having fun with the bug to generate colored messages, dubbed "rainbow tweets". This was achieved by using inline styling to set the same color for the text and background.
Then people realized that the onmouseover= event can be similarly abused to execute JavaScript whenever the mouse pointer rolls over the message.
Initially, this trick was used to launch innocent pop-up boxes. However, it was only a matter of time until someone crafted a tweet, that forces logged in users to re-repost it.
"It looks like many users are currently using the flaw for fun and games, but there is obviously the potential for cybercriminals to redirect users to third-party websites containing malicious code, or for spam advertising pop-ups to be displayed," warns Graham Cluley, senior technology consultant at Sophos.
The exploit is hard to avoid even for people who security aware, because once such a tweet appears in the feed, it's very easy to accidentally roll over it with the mouse.
The rogue message was seen being re-posted even from the Twitter accounts of security companies and professionals.
Similar vulnerabilities have led to the creation of Twitter XSS or clickjacking worms in the past, but this has to be one of the most viral attacks the platform has ever experienced.
Using the NoScript Firefox extension, which contains powerful anti-XSS protection doesn't help either, because the code is served from twitter.com and most people have already whitelisted the domain.
UPDATE: A new variation of the attack that uses class="modal-overlay" makes it a harder to remove the rogue messages, because the entire page becomes one big clickable link.
One solution is to access your profile via twitter.com/[your_username] and refresh the page until you don't get the dimmed out overlay anymore and you can click on page elements.
At this point be careful not to roll over the whole rogue message again, which should appear as a retweet. Instead, slowly move the mouse over its bottom right corner by approaching it from the right.
You should see an Undo link appear. Click it and the message should dissapear. It might be sensible to stop using Twitter after this, until the problem is resolved.
UPDATE 2: An easier solution is to access http://mobile.twitter.com/[your_username] and remove it from there. Doing the same via TweetDeck and other stand-alone applications also works.
UPDATE 3: Twitter has fixed the vulnerability. "Update (6:50 PDT, 13:50 UTC): The exploit is fully patched," an announcement posted on its official status page reads.
 14 DAY TRIAL //
14 DAY TRIAL //