New brute-force attacks delivered against WordPress websites leverage the XML-RPC protocol and the wp.getUsersBlogs function, it has been revealed.
XML-RPC is a remote procedure call protocol that relies on Extensible Markup Language (XML) for call encoding and on HTTP for transporting.
Daniel Cid, CTO at Sucuri, a company that offers services for preserving the integrity of a website, says that this type of attacks have increased lately, because using XML-RPC works faster and the attempts are more difficult to detect.
He says that this sort of abuse is possible “because many calls in the WordPress XMLRPC implementation required a username and password.” By simply providing a pair of credentials, a reply is returned informing if the combination allows access to the administration panel of the website or not.
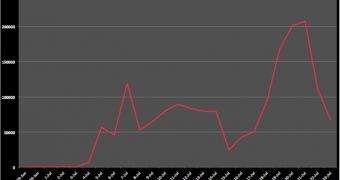
Starting July 4, Sucuri has seen that attacks leveraging these parameters have become more frequent. The numbers are impressive, with a ten-fold increase since the beginning of the month: two million attempts originating from 17,000 different IP addresses.
Cid reports that the company’s systems have even seen a total of almost 200,000 attempts in some days.
However, he said that “the only reason these numbers are not higher is because we’re killing the logs after block attempts, so all you are seeing is the gradual increase in attacks, but not the complete picture.”
It seems that the attackers used the “admin” username only in 167,000 attempts, out of the two million mentioned earlier. Other options in the dictionary used by the preps of the brute-force attacks include the domain name or some variations of the targeted website.
Cid provides a list of the passwords in the dictionary, which are common countersigns available in many dictionaries: “1dc13d,” “admin,” “123123,” “admin1,” “admins,” “123456,” “12345678,” “7777777,” “letmein,” “121212,” “qweqwe,” “iloveyou” or “administrator.”
According to Sucuri, website administrators looking for a solution against this sort of abuse can rely on multiple methods; those having a dedicated server can install OSSEC, an open-source host-based intrusion detection system (HIDS) and configure it to reject connection from any IP that fails to login on multiple attempts.
Daniel Cid mentions other forms of protection, such as WordPress plugins, but it seems that during his tests none of the tried ones managed to offer protection against XML-RPC calls.
WordPress websites have recently been attacked through a vulnerability of the MailPoet plugin, attackers being able to compromise thousands of websites running an unpatched version of the component.
 14 DAY TRIAL //
14 DAY TRIAL //